Free Email Extractor 5.7 cracked
The proliferation of cracked Email Extractor 5.7 tools has significantly contributed to the escalation of cyberattacks, particularly in the realm of data harvesting and phishing campaigns. One such tool, a widely distributed email extraction utility, is often exploited in its cracked form to bypass licensing restrictions, enabling threat actors to harvest email addresses end masse for malicious purposes. These activities usually result in spam campaigns, credential stuffing attacks, and targeted social engineering exploits. The cracked version, stripped of security checks, further poses risks by potentially bundling additional malware, turning a seemingly benign tool into a vector for compromise.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
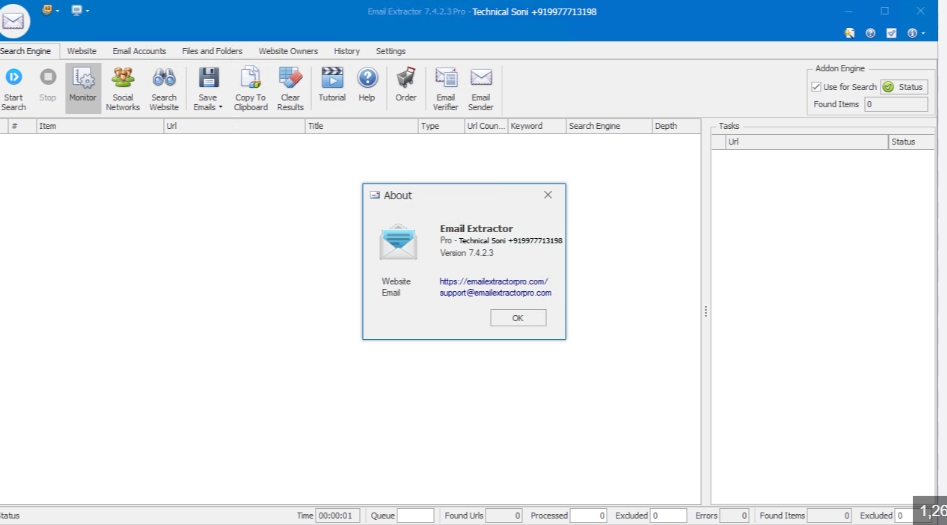
This software is designed to extract email addresses from various sources, including websites, documents, and local files, primarily for marketing and lead generation purposes. Legitimate users, such as digital marketers, rely on it to compile contact lists efficiently and effectively. However, when cracked or misused, the tool becomes a potent weapon for cybercriminals seeking to gather large volumes of email addresses for spam, phishing, or brute-force attacks. Its ability to parse data rapidly and export it in multiple formats makes it attractive for both ethical and malicious use cases.
Key Features of Email Extractor 5.7
| Feature | Description |
| Web Crawling | Scrapes websites to collect visible email addresses from pages and subdomains. |
| Document Parsing | Extracts emails from files (PDFs, Word, Excel) by scanning text content. |
| Regex Filtering | Uses pattern matching to identify valid email formats and exclude irrelevant data. |
| Export Options | Saves extracted emails in CSV, TXT, or database formats for easy integration. |
| Batch Processing | Handles large datasets or multiple files simultaneously for efficiency. |
| Proxy Support | Allows anonymized scraping by routing requests through proxy servers. |
How Email Extractor 5.7 Works
The tool operates through a combination of automated web crawling, document parsing, and data filtering techniques. Below is a breakdown of its core functionality:
Data Collection
- Web Scraping: The software sends HTTP requests to target URLs, downloads page content, and scans for email patterns using regular expressions (Regex). Advanced versions may follow hyperlinks to crawl entire websites recursively.
- Document Processing: For local files, it utilizes text extraction libraries to read content and apply regular expressions (Regex) to isolate email addresses.
Filtering and Validation
- Extracted data is filtered to remove duplicates and invalid entries. Some versions integrate SMTP verification to check email validity by simulating a mail server handshake (without sending actual emails).
Payload Delivery (Malicious Use Cases)
- In cracked versions, attackers may embed additional malware, such as keyloggers or backdoors, which execute upon installation. The software might also connect to a command-and-control (C2) server to exfiltrate harvested data or download secondary payloads.
- Export files (e.g., CSV) could be weaponized with macros or malicious scripts to spread malware when opened by the victim.
Evasion Techniques of Email Extractor 5.7
- To avoid detection, the tool may utilize proxies or Tor to conceal its scraping activities. Cracked variants often turn off update checks, leaving users vulnerable to unpatched exploits.
By automating email harvesting and simplifying data aggregation, this software, especially in unauthorized forms , poses significant risks when wielded by malicious actors. Its dual-use nature underscores the importance of monitoring such tools in cybersecurity defenses.