Frutas rat english 2024
Frutas RAT English 2024 is an emerging Remote Access Trojan that has gained notoriety for its lightweight design and effective evasion capabilities. Originally developed in Spanish-speaking hacking communities, this English version now poses a global threat with improved functionality. Unlike more complex RATs, Frutas maintains a low profile while providing comprehensive system control, making it particularly dangerous for persistent attacks.

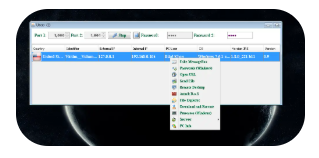
What is Frutas RAT English 2024?
Frutas RAT is a Windows-based remote administration tool repurposed for unauthorized access, distributed through underground hacking forums and phishing campaigns. The 2024 English version features enhanced anti-detection mechanisms and a simplified interface that appeals to less technical hackers. It specializes in credential harvesting, surveillance, and backdoor access while maintaining a small footprint to avoid detection.
Detailed Features of Frutas RAT English 2024
| Feature Category | Technical Specifications |
|---|---|
| Remote Control | Desktop viewing, mouse/keyboard control, and process management |
| File Management | Download/upload files, execute programs, modify system files |
| Surveillance | Screenshot capture, webcam activation, microphone recording |
| Data Collection | Password extraction from browsers, email clients, and FTP software |
| Network Tools | Port scanning, WiFi credential harvesting, network mapping |
| Persistence | Registry autorun entries, scheduled tasks, service installation |
| Evasion Techniques | Process hollowing, junk code injection, basic sandbox detection |
| Communication | TCP/UDP protocols with basic XOR encryption for C2 traffic |
| Keylogging | Logs keystrokes including secure input fields |
| Plugin Support | Supports third-party modules for expanded functionality |
Why Do Hackers Use Frutas RAT English 2024?
Easy to Use – Simple interface requires minimal technical knowledge to operate
Lightweight – Small file size (often <2MB) helps avoid detection
Effective Persistence – Multiple installation methods ensure long-term access
Versatile Targeting – Works equally well on home users and corporate networks
Cost Effective – Often distributed freely or at low cost in hacking communities


