Gmail Bruteforce 2024
Gmail Bruteforce 2024 refers to sophisticated tools and techniques designed to crack Gmail passwords through automated trial-and-error methods. While these tools have legitimate use cases in cybersecurity assessments, they are also exploited by malicious actors to gain unauthorized access. This article explores how Gmail Bruteforce 2024 works, its advanced features, ethical considerations, and preventive strategies.
Download Link 1
Download Link 2
Download Link 3
Download Link 4

What is Gmail Bruteforce 2024?
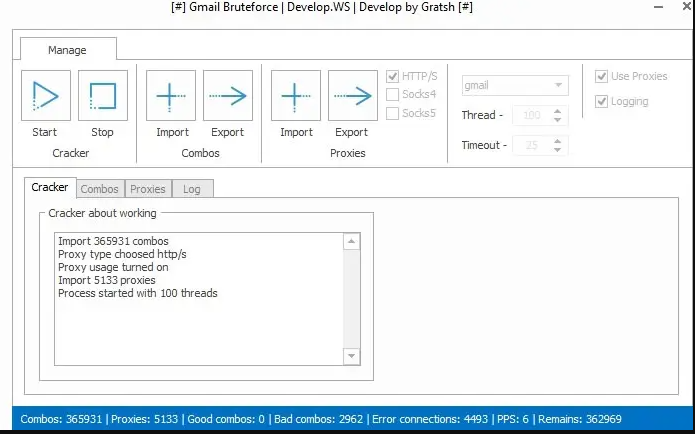
Gmail Bruteforce is an advanced form of password-cracking that leverages modern computing power, AI-enhanced algorithms, and proxy networks to bypass Gmail’s robust security mechanisms. Unlike traditional brute-force tools, this version uses predictive analytics and machine learning to optimize password guessing, making it both efficient and dangerous when misused.
Key Features
| Feature | Description |
|---|---|
| AI-Powered Password Guessing | Utilizes machine learning to predict password patterns and generate likely guesses. |
| Proxy & VPN Support | Rotates IP addresses using SOCKS5/HTTP proxies to evade rate-limiting and IP bans. |
| Multi-Threaded Attacks | Executes hundreds of login attempts per second using parallel threads. |
| Custom Wordlists | Integrates popular leaked password lists like RockYou and HIBP for targeted attacks. |
| CAPTCHA Bypass | Uses OCR solvers or APIs to defeat Google’s CAPTCHA challenges. |
| Session Hijacking | Exploits stolen cookies or tokens to access Gmail without password entry. |
| Stealth Mode | Imitates human typing behavior and timing to avoid detection. |
| 2FA Bypass Techniques | Attempts to circumvent two-factor authentication using phishing or SIM-swapping. |
Legitimate Uses of Gmail Bruteforce 2024
While its potential for misuse is high, Gmail Bruteforce 2024 has legitimate applications in cybersecurity:
- Ethical Hacking: Used by penetration testers to assess email security in organizations.
- Password Recovery: A last resort for recovering access to one’s account (with authorization).
- Security Research: Helps researchers understand vulnerabilities and develop defenses.
- Forensic Investigations: Employed by law enforcement during authorized digital investigations.


