HiveRAT Cracked 2025
In the underground cybercrime ecosystem, cracked versions of legitimate remote administration tools have become a growing threat when weaponized for malicious purposes. One such modified HiveRAT Cracked 2025 variant has gained notoriety among threat actors for its enhanced stealth capabilities and affordability on dark web markets. This repurposed software exemplifies how cybercriminals are leveraging cracked security tools to conduct sophisticated attacks while avoiding the costs and development efforts of creating custom malware. Its widespread availability has lowered the barrier to entry for aspiring hackers, contributing to its proliferation in credential theft campaigns, corporate espionage, and ransomware operations.
Download Link 1
Download Link 2
Download Link 3
Download Link 4

What is this modified HiveRAT Cracked 2025?
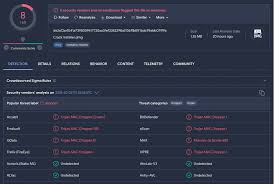
This is a cracked version of a commercial remote administration tool that has been stripped of its security protections and augmented with additional malicious features. Unlike its legitimate counterpart, this unauthorized variant includes built-in obfuscation techniques, persistence mechanisms, and anti-analysis capabilities specifically designed for covert operations. Cybercriminals primarily use it to establish backdoor access to compromised systems, often deploying it through phishing campaigns or exploit kits. The software’s dual-use nature makes it particularly dangerous, as some components appear legitimate while containing hidden malicious functionality.
Key Features
| Feature | Description |
| Silent Installation | Executes without user interaction or visible installation prompts |
| Process Hollowing | Injects malicious code into legitimate system processes |
| Encrypted C2 Channels | Uses TLS and custom encryption for communication |
| Credential Theft Module | Harvests browser passwords and authentication cookies |
| Screen Streaming | Provides real-time desktop viewing with low detection risk |
| Fileless Execution | Operates in memory without dropping executable files |
| UAC Bypass | Elevates privileges without triggering User Account Control |
| Persistence | Maintains access through registry modifications and service creation |
| Anti-Sandbox | Detects and evades virtualized analysis environments |
How It Works
Initial Compromise
- Weaponized office documents with malicious macros.
- Fake software updates are bundled with the payload.
- Compromised legitimate websites serve drive-by downloads.
- Malvertising campaigns redirect to exploit kits.
Execution Phase
- Conducts environment checks for virtual machines or analysis tools.
- Deploys multiple layers of obfuscation to hinder static analysis.
- Uses process injection to run within trusted applications like explorer.exe.
Persistence Establishment
- Creates scheduled tasks with randomized names.
- Modifies registry Run keys and Windows Management Instrumentation (WMI) events.
- It installs itself as a Windows service with deceptive descriptions.
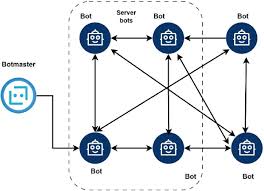
Command and Control
- Encrypted WebSocket connections to blend with normal traffic.
- Domain generation algorithms (DGA) for resilient C2 infrastructure.
- Fallback mechanisms using cloud storage services as backup channels.
Malicious Operations
- Deploy additional payloads like ransomware or cryptominers.
- Harvest credentials from memory and security vaults.
- Log keystrokes and capture screenshots at timed intervals.
- Manipulate network settings for man-in-the-middle attacks.
- Disable security software using a legitimate process termination.
Evasion Techniques
- API unhooking to bypass security product monitoring.
- Reflective DLL loading to avoid disk writes.
- Time-based triggers that delay malicious activity.
- Cleanup routines that remove initial infection vectors.
- Code polymorphism that alters signatures between infections.