Layer 4 DDOS Tool Python 2024
Distributed Denial-of-Service (DDoS) attacks continue to pose a persistent threat in cybersecurity, with Layer 4 attacks being particularly disruptive due to their ability to overwhelm network resources. In 2024, a Python-based DDoS tool gained attention for its efficiency in launching high-volume attacks by exploiting transport-layer protocols. Such tools are frequently used in cyberattacks to disrupt services, extort organizations, or distract security teams while other malicious activities occur. Layer 4 DDOS Tool accessibility and customizable nature make them a preferred choice for both novice and advanced threat actors.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
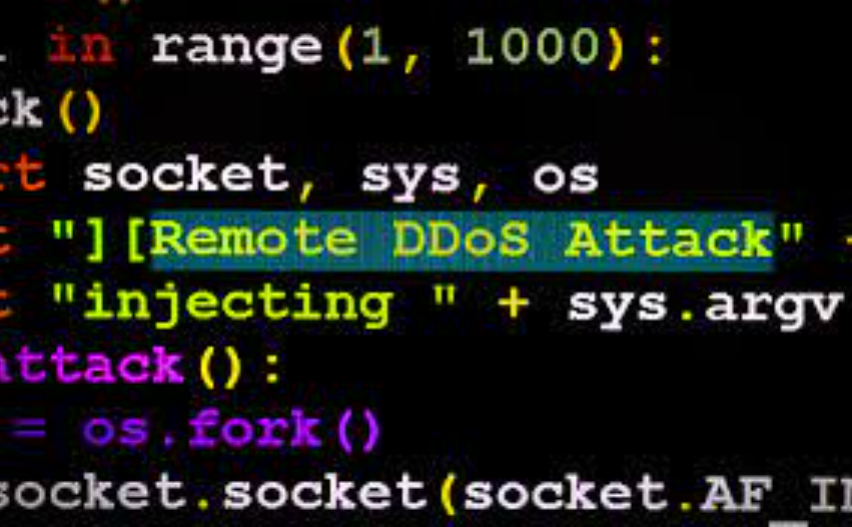
Layer 4 DDOS Tool is a Python script designed to orchestrate Layer 4 DDoS attacks, primarily targeting TCP and UDP protocols. It leverages multiple techniques to flood a victim’s network with traffic, exhausting bandwidth, connection limits, or server resources. Typically, it is used in penetration testing (with proper authorization) but is often repurposed for malicious attacks. The tool supports various attack vectors, including SYN floods, UDP floods, and amplification attacks, making it adaptable to different scenarios.
Key Features of Layer 4 DDOS Tool
| Feature | Description |
| Multi-vector Attacks | Supports SYN, UDP, and other Layer 4 flood techniques. |
| IP Spoofing | Masks the attacker’s IP to evade detection. |
| Botnet Integration | Can coordinate with compromised devices (botnets) for larger-scale attacks. |
| Adjustable Payloads | Allows customization of packet size and transmission rate. |
| Threaded Execution | Uses multi-threading to maximize attack efficiency. |
| Lightweight & Portable | Runs on low-resource systems and is easily deployable. |
How the Layer 4 DDOS Tool
Attack Techniques
The software operates by flooding the target with a high volume of network packets, exploiting weaknesses in the TCP and UDP protocols. Common techniques include:
- SYN Flood: Sends a rapid succession of SYN requests to a target, leaving connections half-open and exhausting server resources.
- UDP Flood: Overwhelms the target with UDP packets, forcing it to process malformed or unresolvable requests.
- Amplification Attacks: Leverages vulnerable servers (e.g., DNS, NTP) to reflect and amplify traffic toward the victim.
Functionality
- Target Specification: The attacker inputs the victim’s IP and port, along with the desired attack method.
- Traffic Generation: The script crafts malicious packets, often randomising source IP addresses (spoofing) to hinder traceback.
- Thread Management: Multiple threads are spawned to increase packet transmission rates, maximizing load on the target.
- Payload Delivery: Depending on the attack type, the payload may consist of SYN packets, garbage UDP data, or crafted requests to amplification servers.
Evasion and Optimization
To avoid immediate detection, the tool may include:
- Rate Limiting: Adjusts packet speed to bypass simple rate-based defenses.
- IP Rotation: Cycles through spoofed IPS to evade blocklisting.
- Protocol Manipulation: Modifies packet headers to appear legitimate.