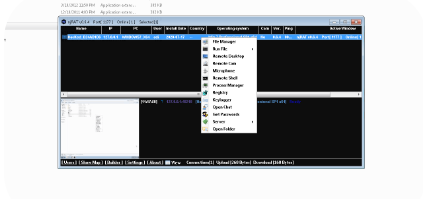
njRAT v0.6.4
njRAT v0.6.4 is a notorious Remote Access Trojan (RAT) that emerged as a significant cybersecurity threat, primarily targeting Windows systems. This malware variant enables attackers to gain complete control over infected machines while evading detection through various obfuscation techniques. While some position it as an administrative tool, its predominant use involves illegal surveillance and data theft operations across numerous cyberattack campaigns.
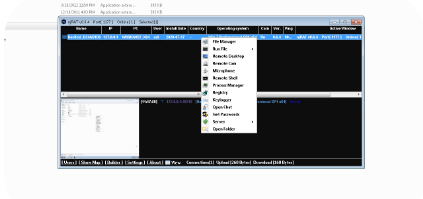
What is njRAT v0.6.4?
njRAT (also known as Bladabindi) is a malicious remote administration tool that first appeared in 2013. Version 0.6.4 represents an evolution in its capabilities, featuring enhanced persistence mechanisms and expanded functionality for system exploitation. Unlike legitimate remote administration software, njRAT operates covertly, often distributed through phishing campaigns, infected downloads, or exploit kits. Its modular architecture allows customization for different attack vectors, making it particularly dangerous in the hands of cybercriminals.
Detailed Features of njRAT v0.6.4
- Remote System Control – Provides attackers with complete command execution privileges on compromised systems
- File Management System – Enables file upload/download, modification and deletion operations on victim machines
- Keylogging Functionality – Records keystrokes to harvest credentials, financial information and sensitive communications
- Screen Capture Capabilities – Takes periodic screenshots or enables real-time desktop viewing
- Webcam Activation – Secretly activates connected cameras for unauthorized surveillance
- Process Manipulation – Can terminate security-related processes or inject malicious code into legitimate applications
- Persistence Mechanisms – Maintains presence through registry modifications and hidden startup entries
- Password Recovery – Extracts saved credentials from browsers, email clients and FTP applications
- DDoS Functionality – Can coordinate infected systems to launch distributed denial-of-service attacks
- USB Propagation – Spreads automatically to removable drives for lateral movement
- Anti-Analysis Techniques – Includes basic virtual machine detection and debugging evasion methods
Why Use njRAT v0.6.4?
While njRAT demonstrates technical sophistication, its primary applications are malicious. Ethical hackers should note that using such tools without explicit authorization violates computer crime laws worldwide. For legitimate security testing, professionals should utilize approved frameworks like Metasploit, Covenant C2, or commercial alternatives with proper licensing. The cybersecurity community strongly discourages experimentation with njRAT due to its association with criminal activities and potential legal consequences.


