NordVPN Checker 2025
In 2025, as VPN services become increasingly essential for privacy and security, cybercriminals have developed specialized tools to exploit these very protections. Among these, credential-checking utilities targeting premium VPN accounts have emerged as a significant threat. NordVPN Checker 2025 tools allow attackers to validate stolen or leaked credentials, gaining access to private networks while hiding behind legitimate VPN infrastructure. The anonymity provided by compromised VPN accounts enables more sophisticated attacks, from credential stuffing to ransomware deployment, while making attribution significantly more difficult for security teams.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
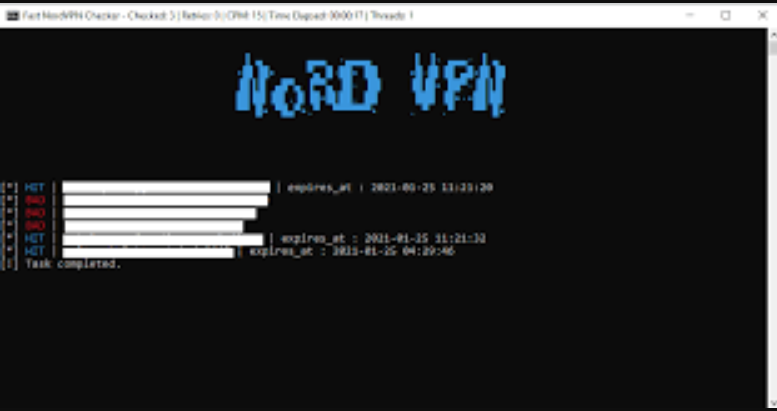
This software is a specialized utility designed to test the validity of VPN service credentials, specifically targeting one of the most popular consumer VPN providers. It automates the process of checking username/password combinations against the VPN’s authentication servers, identifying active accounts that can be hijacked. While penetration testers might use similar tools for security audits, malicious actors primarily deploy it to build inventories of compromised premium VPN accounts. These stolen credentials are then used to mask malicious activities or sold on underground markets, often bundled with other stolen data packages.
Key Features
| Feature | Description |
| Bulk Credential Checking | Tests thousands of credentials simultaneously against VPN auth servers |
| Proxy Integration | Routes checks through multiple proxies to avoid detection |
| Speed Optimization | Implements connection pooling and parallel testing for efficiency |
| Live Session Detection | Identifies currently active VPN sessions for account takeover |
| Geolocation Spoofing | Tests credentials from various geographic regions to mimic normal usage |
| API Abuse | Exploits VPN provider’s mobile/desktop app APIs for stealthier checking |
| Result Filtering | Categorizes accounts by subscription level and remaining validity period |
How NordVPN Checker 2025 Works
1. Credential Preparation
- Accepts input lists combining emails and passwords (typically from previous breaches)
- Cleans data by removing malformed entries and known invalid credentials
- Organizes credentials by domain patterns for more efficient checking
2. Authentication Process
- Establishes connections to VPN provider’s authentication endpoints
- Uses official API protocols to mimic legitimate client software
- Tests credentials using both traditional auth methods and OAuth flows
- Captures detailed responses to distinguish between:
- Valid credentials
- Valid credentials with active sessions
- Expired subscriptions
- Rate-limited or blocked attempts
3. Evasion Techniques
- Rotates source IP addresses using residential proxy networks
- Randomizes time intervals between checks (100-1500ms)
- Spoofs device fingerprints (mobile vs desktop clients)
- Varies TLS fingerprinting to avoid pattern detection
- Distributes load across multiple VPN endpoints
4. Post-Verification Processing
For valid accounts, the tool can:
- Extract remaining subscription duration
- Identify concurrent connection limits
- Check for active sessions (potential takeover opportunities)
- Test server availability across different countries
- Verify protocol support (OpenVPN, WireGuard, etc.)
5. Advanced Features
More sophisticated versions include:
- Session Hijacking: Disconnects active sessions to claim accounts
- Configuration Export: Generates ready-to-use .ovpn files
- Automated Resale: Lists valid accounts on underground markets via API
- Traffic Mirroring: Routes a percentage of checks through already-valid accounts
Security Implications
Attack Advantages:
- Provides attackers with clean, residential-looking IP addresses
- Enables bypassing of geographic restrictions and IP blacklists
- Creates difficult-to-trace infrastructure for subsequent attacks
- Allows testing stolen credentials against multiple services simultaneously


