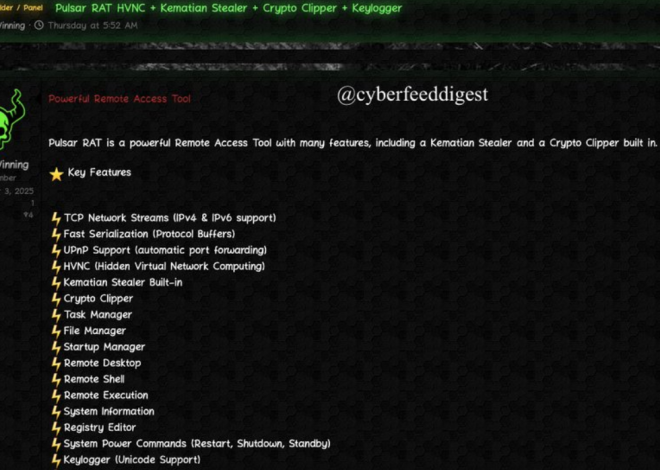
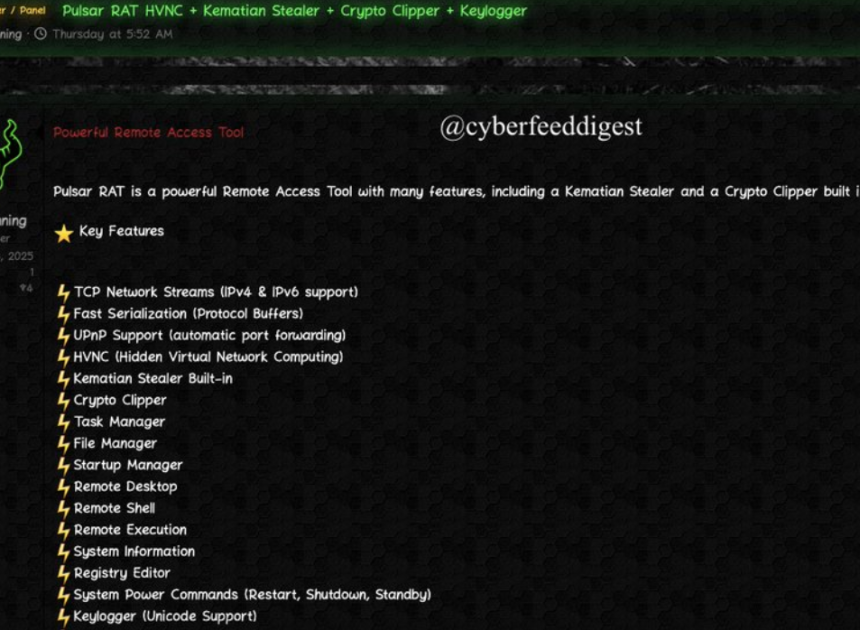
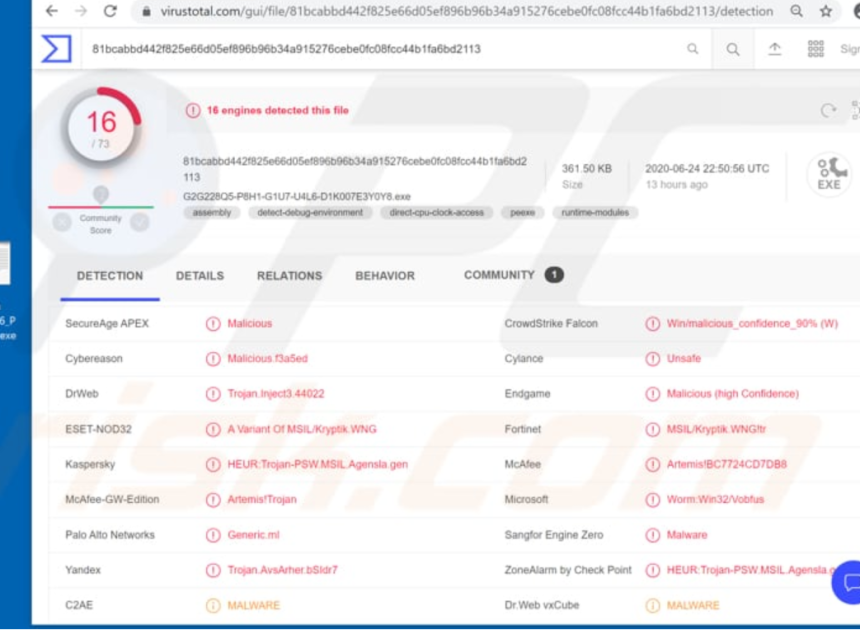
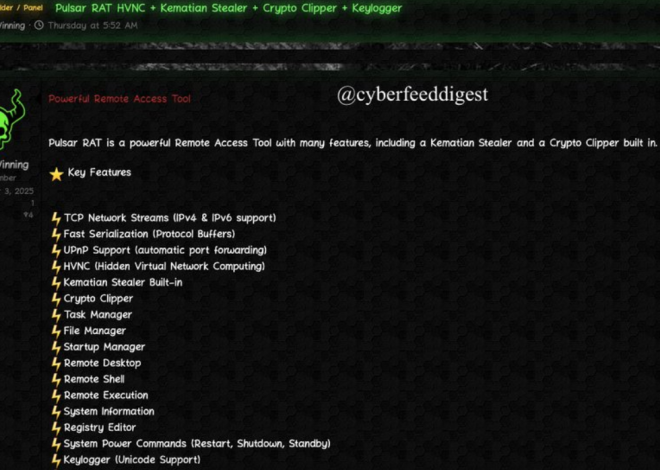
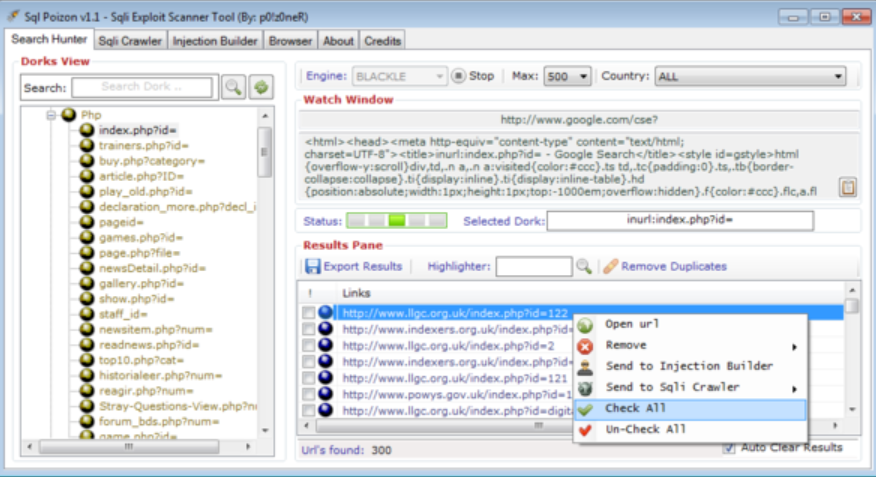
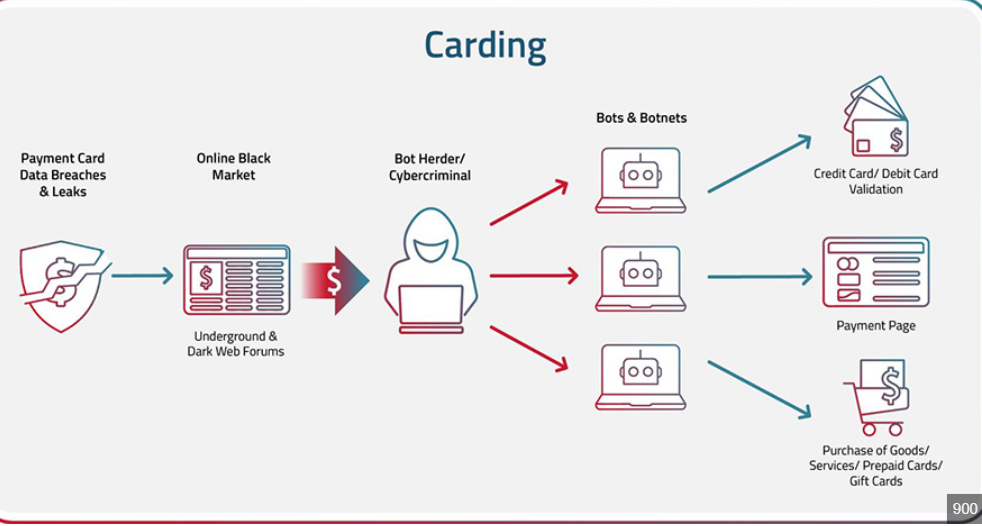
Carding and Hacking Tools 2024
Cyberattacks continue to evolve in sophistication, leveraging advanced tools to exploit vulnerabilities in systems and networks. Among these tools, carding and hacking software has become a significant threat, enabling malicious actors to conduct financial fraud, data breaches, and unauthorized access at scale. The “Carding and Hacking Tools 2024” category represents a collection of modernized utilities […]
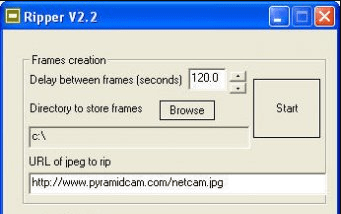
Mail Ripper 2024
Email remains one of the most exploited attack vectors in 2024, with cybercriminals constantly developing new tools to bypass security measures. Among these threats, specialized email cracking utilities have become particularly dangerous, enabling attackers to systematically compromise email accounts through brute-force and credential-stuffing techniques. Consequently, tools like Mail Ripper 2024 pose a significant threat to […]
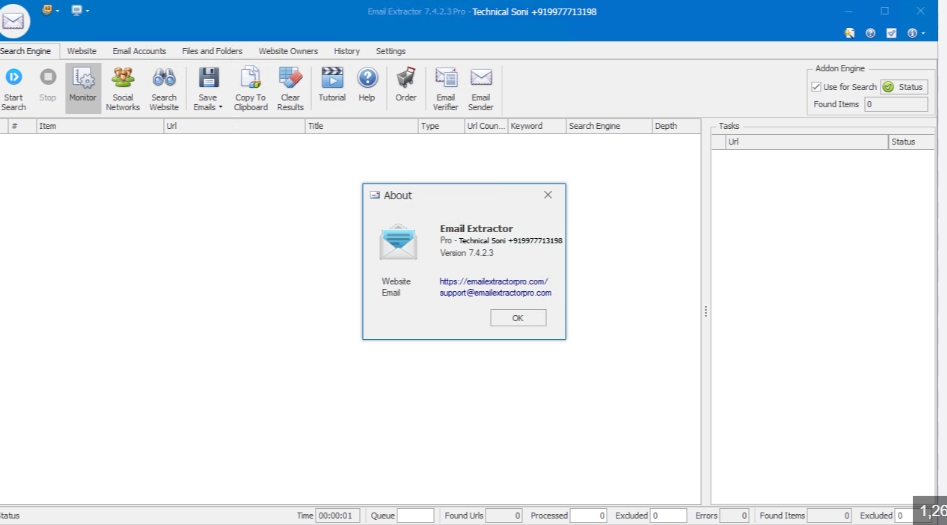
Free Email Extractor 5.7 cracked
The proliferation of cracked Email Extractor 5.7 tools has significantly contributed to the escalation of cyberattacks, particularly in the realm of data harvesting and phishing campaigns. One such tool, a widely distributed email extraction utility, is often exploited in its cracked form to bypass licensing restrictions, enabling threat actors to harvest email addresses end masse […]
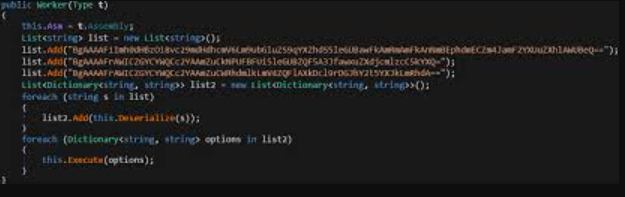
SILVERBULLET PRO V1.0
The cybersecurity landscape in 2024 has witnessed the emergence of increasingly sophisticated automated attack platforms, enabling cybercriminals to launch complex campaigns with unprecedented efficiency. Among these, professional-grade exploitation tools have become particularly dangerous due to their modular design, evasion capabilities, and user-friendly interfaces. The SILVERBULLET PRO V1.0 platform has lowered the technical barrier for entry […]
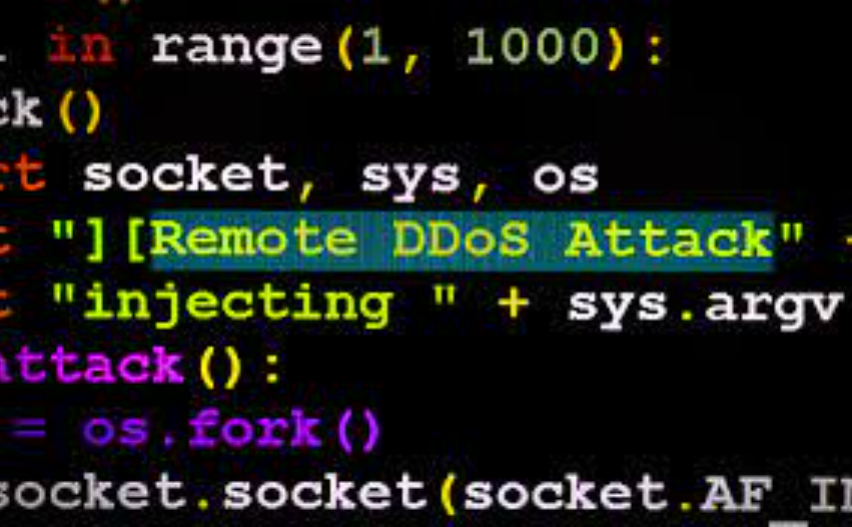
Layer 4 DDOS Tool Python 2024
Distributed Denial-of-Service (DDoS) attacks continue to pose a persistent threat in cybersecurity, with Layer 4 attacks being particularly disruptive due to their ability to overwhelm network resources. In 2024, a Python-based DDoS tool gained attention for its efficiency in launching high-volume attacks by exploiting transport-layer protocols. Such tools are frequently used in cyberattacks to disrupt […]
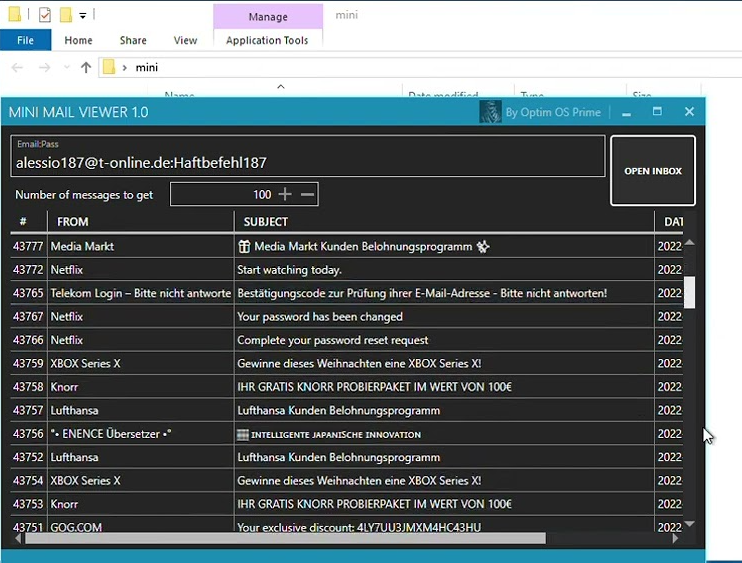
Mini Mail Viewer 2.0
Email remains one of the most targeted attack vectors in cybersecurity, with threat actors constantly developing tools to exploit email clients and protocols. In 2024, specialised email monitoring utilities have been repurposed by malicious actors to facilitate unauthorised access to sensitive communications. Mini Mail Viewer 2.0 tools pose a significant threat to both individual privacy […]
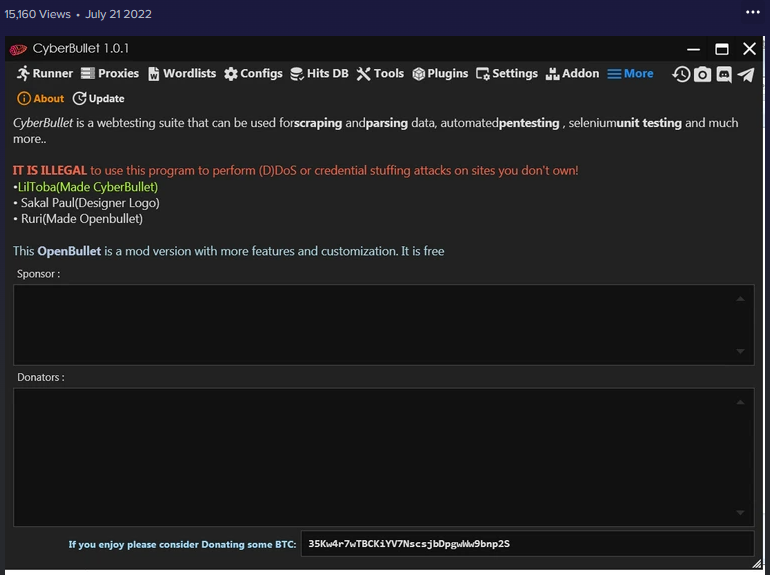
CyberBullet V1.0.1
The cybersecurity threat landscape in 2024 has witnessed the rise of increasingly sophisticated attack tools that combine automation, evasion techniques, and modular exploit capabilities. Among these, a new generation of multi-purpose attack platforms has emerged, enabling cybercriminals to conduct complex campaigns with unprecedented efficiency. CyberBullet V1.0.1 has become particularly dangerous due to its ability to […]
Advance Bulk Mailer 4.5 Cracked
Cybercriminals increasingly rely on cracked or pirated software to distribute malware, evade detection, and automate malicious campaigns. For instance, one such tool, often referred to as an “Advance Bulk Mailer 4.5 Cracked” version, has been repurposed by threat actors to conduct spam campaigns, phishing attacks, and malware distribution. Although the original software may have legitimate uses, cracked […]
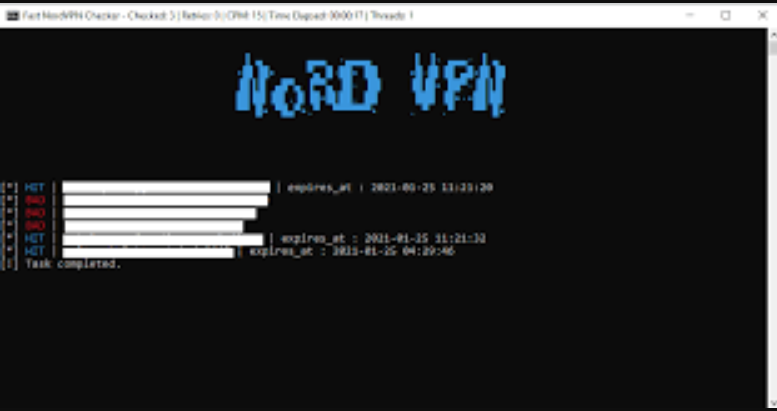
NordVPN Checker 2025
In 2025, as VPN services become increasingly essential for privacy and security, cybercriminals have developed specialized tools to exploit these very protections. Among these, credential-checking utilities targeting premium VPN accounts have emerged as a significant threat. NordVPN Checker 2025 tools allow attackers to validate stolen or leaked credentials, gaining access to private networks while hiding […]
Improved RedLine Clipper 2025 Cracked
In the ever-evolving world of cybercrime, attackers are constantly refining their tools to exploit digital transactions, particularly those involving cryptocurrencies. One of the most insidious threats to emerge in recent years is an advanced form of malware designed to hijack cryptocurrency transfers by manipulating clipboard data. This sophisticated evolution of traditional Improved RedLine clipper 2025 […]