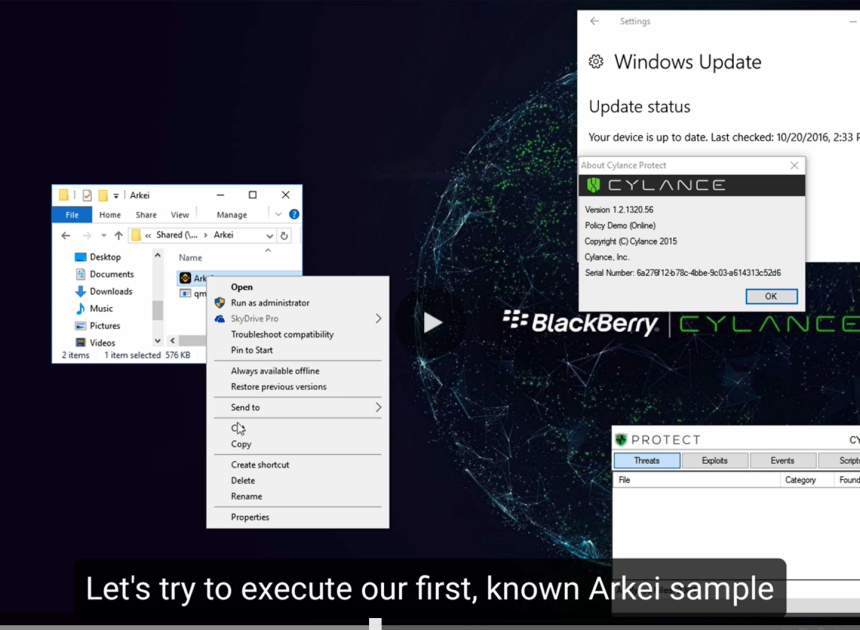
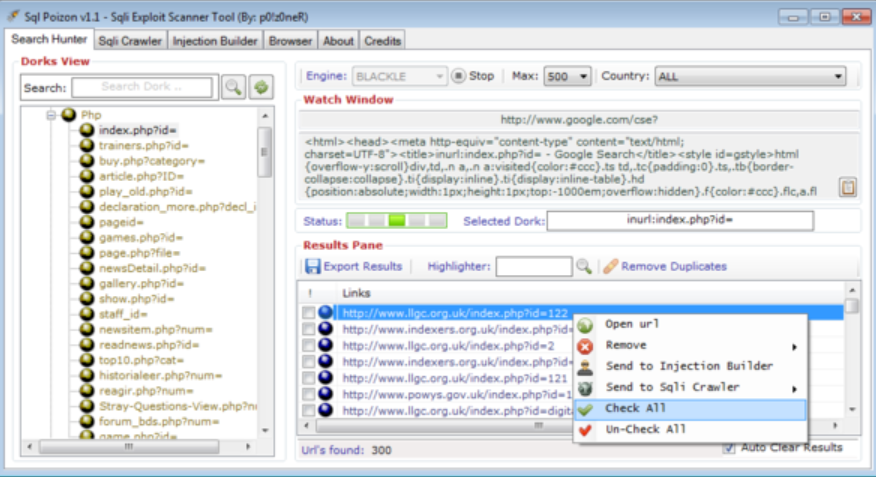
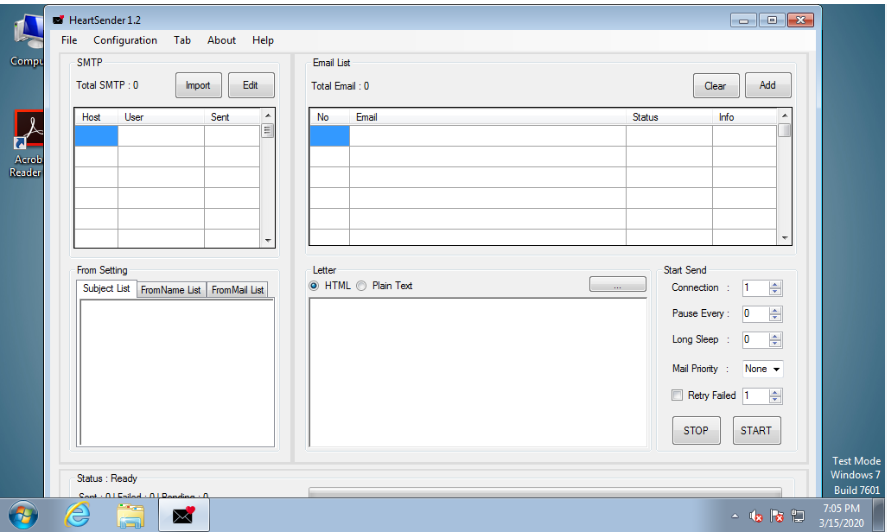
Heart Sender 3.0 Cracked
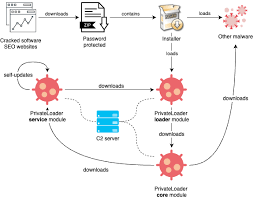
Cybercriminals are increasingly relying on cracked versions of legitimate tools to carry out sophisticated attacks, thereby evading detection while exploiting the powerful functionalities of these tools. One such example is Heart Sender 3.0 Cracked, a modified version of a commercial email marketing tool that has been repurposed for malicious campaigns. These cracked tools often bypass […]
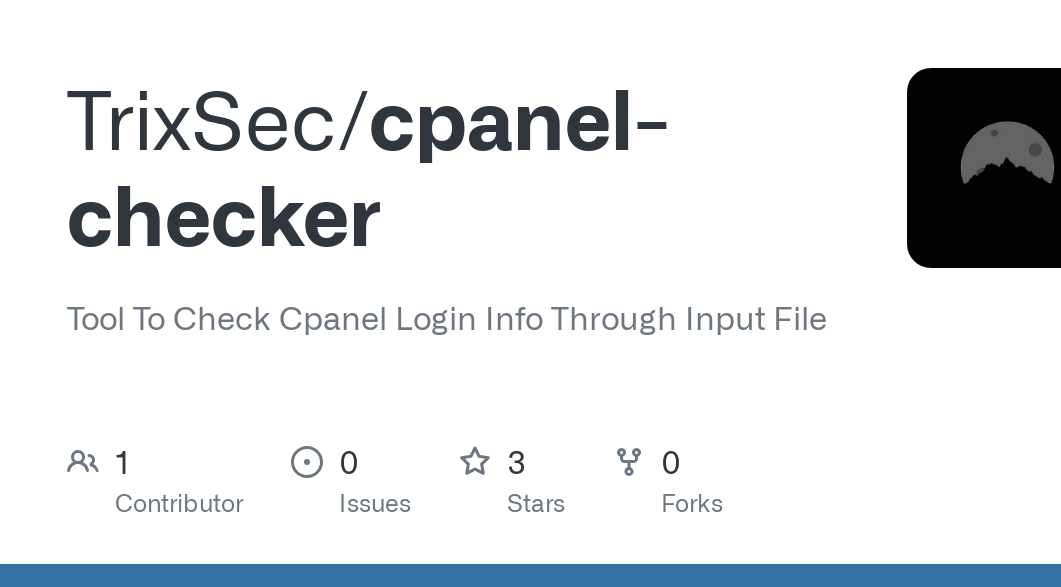
Cpanel Checker Account 2025
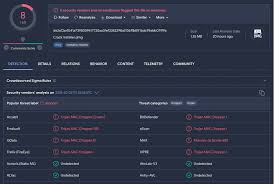
As web hosting control panels remain critical infrastructure for millions of websites, specialized tools have emerged to target these administrative interfaces. In 2025, credential testing tools focusing specifically on hosting control panels have become increasingly sophisticated, posing significant risks to web infrastructure security. These tools enable attackers to systematically probe for vulnerable accounts, often serving […]
HACK PACK Crypters, Binders, Keyloggers and more
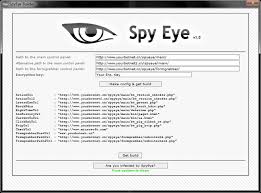
Modern cybercriminals increasingly rely on all-in-one attack toolkits that bundle multiple malicious capabilities into single, easy-to-use platforms. These Swiss Army knife-style packages have become particularly dangerous as they democratize advanced attack techniques, enabling even low-skilled threat actors to launch sophisticated campaigns. By combining HACK PACK crypter, binder, and keylogger functionalities with automated deployment mechanisms, these […]
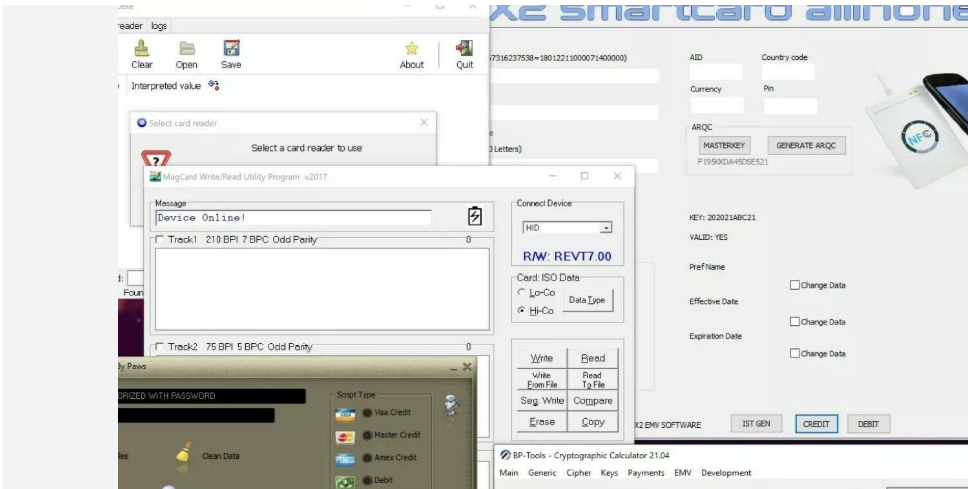
x2 2021 Emv Writer
In recent years, advanced malware-writing tools have emerged as a significant threat to the cybersecurity landscape. Among these, x2 2021 Emv Writer has gained notoriety for its role in facilitating sophisticated cyberattacks, particularly in financial fraud and data theft. These tools empower attackers to create and deploy malicious payloads with relative ease, often bypassing traditional […]
Exploit Office Macro 2025
Exploit Office Macro 2025 attacks have re-emerged as one of the most prevalent infection vectors in modern cyberattacks, despite increased security awareness and defensive measures. These attacks capitalize on the powerful scripting capabilities built into productivity software while exploiting the trust users place in common document formats. The 2025 generation of macro-based attack tools demonstrates […]
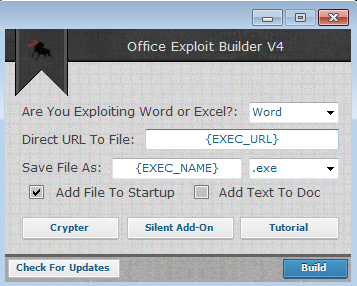
Office Exploit Builder Cracked 2025
Office Exploit Builder delivery has seen a resurgence in modern cyberattacks, with threat actors increasingly leveraging weaponized Office documents as their initial infection vector. The availability of sophisticated exploit builders has significantly simplified the process of creating malicious documents that can bypass security controls. Cracked versions of these tools circulating in underground forums have lowered […]
NJRAT Red Version Error 404
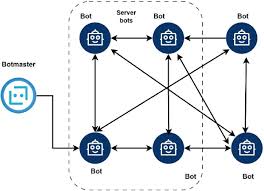
In the ever-evolving world of cyber threats, Remote Access Trojans (RATs) remain a persistent and dangerous tool for attackers. Among these, a well-known NJRAT Red Version —often referred to by its alias—has gained notoriety for its flexibility and widespread use in cyberattacks. This malware enables attackers to take full control of infected systems, steal sensitive […]
BIG EXPLOIT COLLECTION 2025
In the ever-evolving landscape of cyber threats, BIG EXPLOIT COLLECTION 2025 frameworks have become a favored weapon for both sophisticated threat actors and script kiddies alike. These Swiss Army knife-like toolkits dramatically lower the barrier to entry for cybercriminals by packaging hundreds of weaponized vulnerabilities with automated exploitation capabilities. The 2025 generation of these frameworks […]
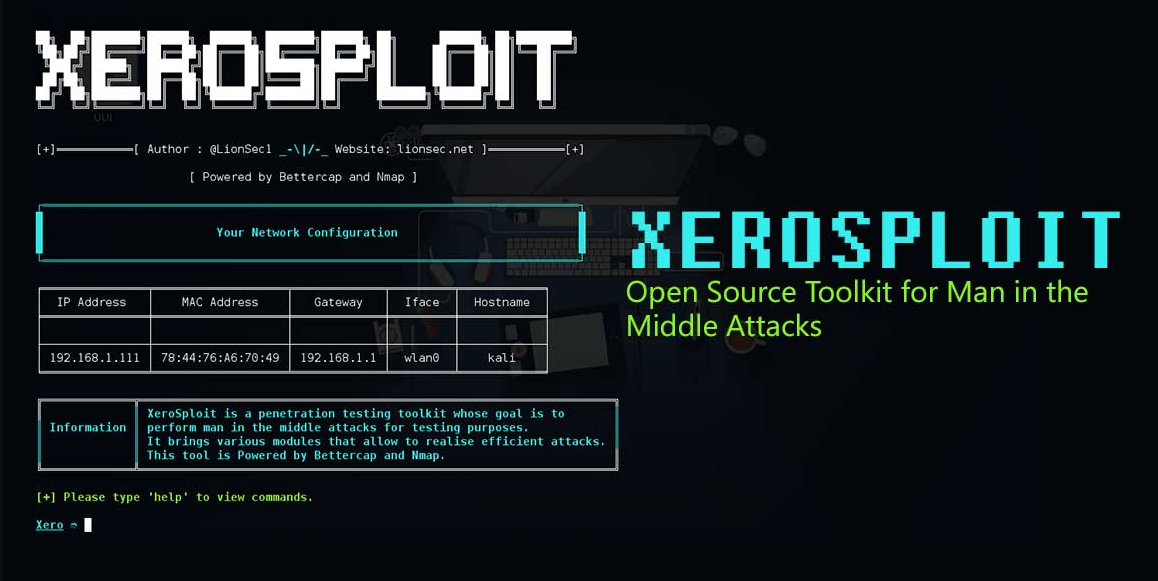
Xerosploit Toolkit 2025
Modern cyberattacks increasingly leverage sophisticated network penetration toolkits that automate man-in-the-middle (MITM) attacks and network exploitation. These frameworks have become particularly dangerous as they enable attackers to intercept, manipulate, and exploit network traffic with minimal technical expertise. When weaponised by malicious actors, Xerosploit Toolkit 2025 can facilitate credential theft, session hijacking, and malware distribution, while […]
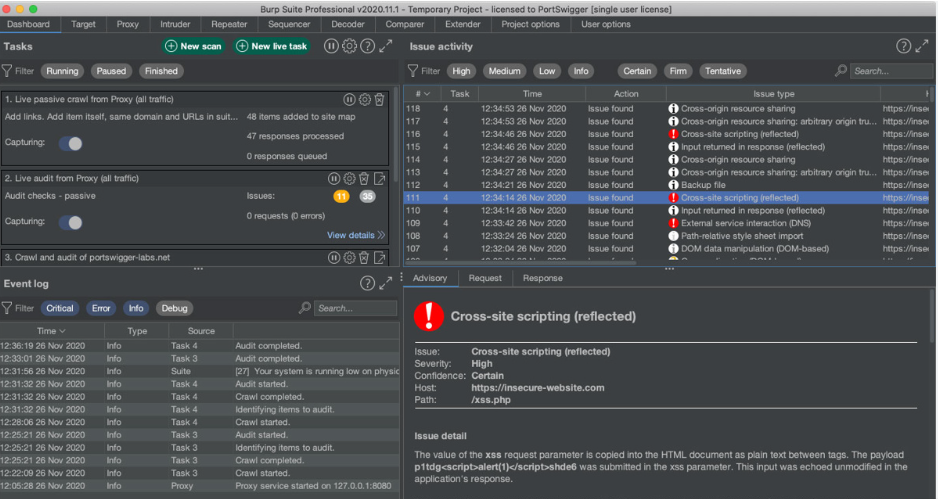
Burp Suite Professional 2022.2.2 Activated
In modern cybersecurity, tools designed for penetration testing and vulnerability assessment are often repurposed by malicious actors to exploit weaknesses in networks and applications. One such tool, Burp Suite Professional 2022.2.2, activated, has become a double-edged sword. While security professionals widely use it to identify and fix vulnerabilities, attackers leverage its capabilities to map attack […]