PEUNION Crypter 2024
In the ever-evolving world of cyber threats, PEUNION Crypter 2024 have become a crucial tool for attackers looking to bypass security measures and deliver malicious payloads undetected. These programs specialise in obfuscating and encrypting malware, making it difficult for traditional antivirus solutions to detect and identify them. Modern cyberattacks, including ransomware, banking trojans, and spyware, frequently rely on crypters to evade detection and maintain persistence on compromised systems. As cybersecurity defences improve, crypters continue to adapt, employing advanced techniques to stay ahead of detection mechanisms.
Download Link 1
Download Link 2
Download Link 3
This software is a sophisticated crypter designed to protect malicious executables from being detected by security software. It works by encrypting and manipulating the structure of malware, enabling it to evade antivirus scans and endpoint protections. Cybercriminals often use it to distribute ransomware, steal sensitive data, or gain remote control over infected machines. While primarily used for malicious purposes, it can also be utilized in ethical penetration testing to assess security vulnerabilities in controlled environments.
Key Features
| Feature | Description |
| Multi-Layer Encryption | Uses multiple encryption algorithms (AES, RC4, XOR) to hide payloads. |
| Anti-Sandbox Bypass | Detects and avoids virtualized or sandboxed environments. |
| Process Injection | Injects payloads into legitimate processes to evade behavioural analysis. |
| Polymorphic Stub | Generates unique decryption stubs for each payload to avoid static detection. |
| Persistence Setup | Establishes long-term access via registry keys, scheduled tasks, or services. |
| Customizable Obfuscation | Allows fine-tuning of obfuscation methods to evade specific AV solutions. |
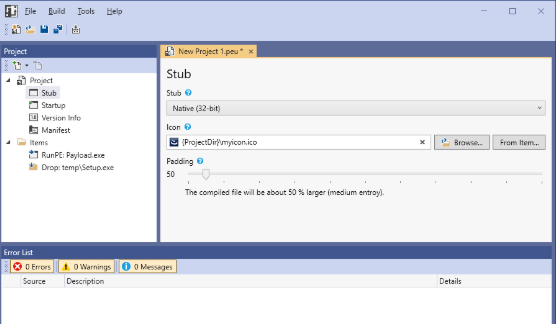
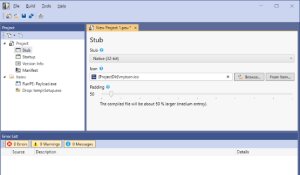
How PEUNION Crypter 2024 Works
The crypter follows a multi-stage process to ensure the payload remains hidden and executes successfully:
- Payload Encryption – The original malware is encrypted using a combination of algorithms (e.g., AES for primary encryption and XOR for additional obfuscation). The encrypted payload is then embedded into a stub file.
- Stub Generation – The stub contains a decryption routine that will unpack the payload in memory. Polymorphic techniques alter the stub’s code structure with each generation, making signature-based detection ineffective.
- Anti-Analysis Checks – Before execution, the stub checks for signs of debugging, sandboxing, or virtual machines. If detected, it may terminate or execute benign code to avoid suspicion.
- Payload Execution – Once in a safe environment, the stub decrypts the payload. It injects it into a legitimate system process (e.g., explorer.exe or svchost.exe) using techniques such as process hollowing or Reflective DLL Injection. This helps the malware blend in with regular system activity.
- Persistence & Evasion – The payload may then establish persistence by modifying registry keys, creating scheduled tasks, or installing itself as a service. Some variants also employ API Unhooking or Direct System Calls to bypass security monitoring tools.
By combining encryption, polymorphism, and stealthy execution techniques, this crypter ensures that malicious payloads remain undetectable until they are successfully deployed. Its ability to evade both static and dynamic analysis makes it a significant challenge for modern cybersecurity defences, highlighting the need for advanced detection methods such as behaviour-based monitoring and machine learning-powered threat analysis.