Pony HTTP Botnet credential-stealing malware
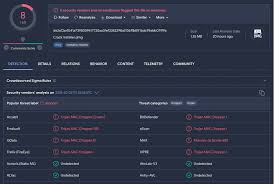
Pony HTTP Botnet is a credential-stealing and botnet malware widely studied by cybersecurity researchers, penetration testers, and ethical hackers. It is designed to harvest usernames, passwords, and digital wallet data while expanding into large-scale botnet networks. By analyzing Pony HTTP Botnet, professionals can understand credential theft, botnet operations, and malware distribution strategies to enhance defensive security measures.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
Key Features of Pony HTTP Botnet
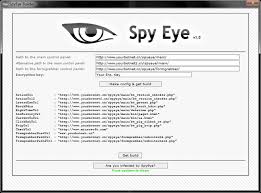
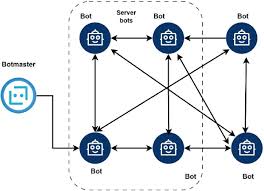
The Pony HTTP Botnet offers advanced features that make it one of the most notorious credential-stealing tools. It allows researchers to study how malware collects usernames, passwords, and other sensitive information from infected systems. Pony supports form-grabbing and credential extraction from web browsers, making it highly effective in simulating real-world phishing and banking attacks. It also enables botnet management, where attackers can control thousands of compromised machines from a centralized command-and-control (C2) server. With its stealth operations, Pony runs silently in the background, evading basic detection techniques while continuously exfiltrating data. Researchers can also study its persistence methods and payload delivery functions, making it an essential platform for learning about credential theft and botnet behavior.
Free Download
Download Pony HTTP Botnet absolutely free from blackhatus.com. An essential tool for malware researchers, penetration testers, and ethical hackers to study credential theft, botnet operations, and strengthen cybersecurity defenses.