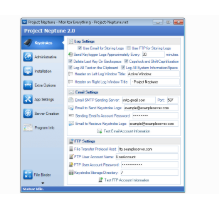
Project Neptune v2.0
Project Neptune v2.0 is a sophisticated credential-harvesting malware designed to stealthily collect sensitive login information from compromised systems. Built with modular architecture and advanced evasion techniques, it primarily targets web browsers, email clients, and financial applications. Its ability to bypass security measures while remaining undetected makes it a significant threat in the cybersecurity landscape.

What is Project Neptune v2.0?
Project Neptune v2.0 is a malware-as-a-service (MaaS) offered on underground hacking forums, allowing threat actors to steal login credentials, session cookies, and authentication tokens. Unlike basic stealers, it employs memory scraping, browser hooking, and encrypted exfiltration to maximize data theft while minimizing detection. Security researchers classify it as a high-risk threat due to its adaptability and effectiveness against modern defenses.
Detailed Features of Project Neptune v2.0
| Feature Category | Description |
|---|---|
| Browser Credential Theft | Extracts saved passwords, cookies, and session tokens from Chrome, Firefox, Edge, Safari, and Opera. |
| Form Grabbing & Keylogging | Captures real-time form submissions (logins, payments) and logs keystrokes for additional credential theft. |
| Two-Factor Authentication (2FA) Bypass | Steals session cookies and OTP tokens to bypass 2FA protections. |
| Email & Messaging App Targeting | Harvests credentials from Outlook, Thunderbird, Discord, and Telegram. |
| Financial Data Extraction | Scrapes banking logins, credit card details, and PayPal credentials from autofill data. |
| Anti-Detection Mechanisms | Uses process injection, API unhooking, and sandbox evasion to avoid AV/EDR detection. |
| Persistence Techniques | Establishes registry modifications, hidden startup tasks, and DLL sideloading for long-term access. |
| Data Exfiltration | Sends stolen data via encrypted channels (HTTPS, Telegram bots, or Discord webhooks). |
| Custom Configuration | Allows buyers to select target applications, evasion methods, and C2 server settings. |
| Remote Update Function | Supports dynamic payload updates without user interaction. |
Why Do Hackers Use Project Neptune v2.0?
High Stealth Capabilities – Uses advanced techniques to evade endpoint detection and response (EDR) solutions.
Broad Compatibility – Works across multiple browsers, email clients, and financial platforms.
Persistent Access – Maintains long-term control over infected systems with hidden persistence mechanisms.
Profitability – Stolen credentials are sold on dark web markets or used in further attacks.
User-Friendly Operation – Comes with a management panel for easy deployment and monitoring.


