RDP Multi Tool Cracked 2025
The rise of remote work has made Remote Desktop Protocol (RDP) a prime target for cybercriminals, leading to the development of increasingly sophisticated attack tools. In 2025, cracked versions of professional RDP exploitation tools have become particularly prevalent in cyberattacks, enabling threat actors to automate large-scale brute-force attacks, vulnerability scanning, and post-compromise activities. RDP Multi Tool Cracked 2025 have lowered the barrier to entry for RDP-based attacks while increasing their effectiveness, contributing to the growing wave of network breaches, ransomware incidents, and data theft operations. Their modular design and automation capabilities allow attackers to scale their operations, targeting everything from small businesses to enterprise networks with equal efficiency.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
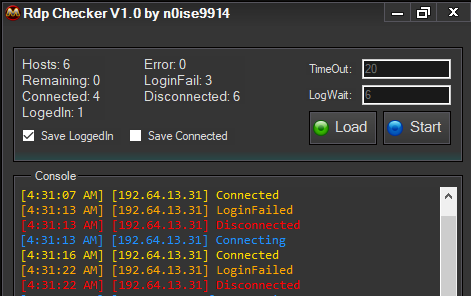
This multi-functional RDP exploitation tool is designed to automate all stages of attacks against Windows remote desktop services. It combines credential testing, vulnerability scanning, and post-exploitation features into a single interface. While network administrators might use legitimate versions for security testing, attackers typically deploy cracked copies to gain unauthorized access to systems, move laterally through networks, and establish persistent backdoors. The software’s effectiveness stems from its ability to bypass common RDP security measures, its support for multiple attack vectors, and its integration with other malicious tools in the attacker’s arsenal.

Key Features
| Feature | Description |
| Multi-threaded Brute-Force | Tests hundreds of credential combinations simultaneously |
| Vulnerability Scanner | Checks for known RDP vulnerabilities (BlueKeep, DejaBlue) |
| Session Hijacking | Steals and reuses active RDP sessions |
| Proxy Support | Rotates IP addresses through multiple proxy layers |
| Credential Spraying | Test common passwords across multiple accounts |
| Automated Lateral Movement | Discovers and exploits network pathways |
| Payload Injection | Deploys malware through established RDP connections |
| GUI Interface | User-friendly dashboard for managing attacks |
How RDP Multi Tool Cracked 2025 Works
- Target Acquisition and Scanning
- Accepts input as IP ranges, domain lists, or specific hostnames
- Scans target networks for open RDP ports (default 3389)
- Fingerprints RDP service versions and configurations
- Identifies vulnerable RDP implementations
- Credential Testing Phase
- Test credentials using multiple methods:
- Traditional brute-force with custom dictionaries
- Credential spraying (testing common passwords across many accounts)
- Known credential testing (reusing breached username/password pairs)
- Handles network timeouts and connection limits
- Bypasses account lockout policies through:
- Timing randomization
- IP rotation
- Multiple account targeting
- Vulnerability Exploitation
- For vulnerable RDP implementations:
- Exploits known CVEs to gain access without credentials
- Bypasses authentication on unpatched systems
- Escalates privileges on compromised hosts
- Deploys initial access payloads:
- Reverse shells
- Web proxies
- Keyloggers
- Session Establishment
- For successful connections:
- Captures session details and credentials
- Takes screenshots of remote sessions
- Record keyboard input
- Disables security notifications
- Post-Exploitation Activities
- Automated network reconnaissance:
- Discovers additional RDP hosts
- Maps network topology
- Identifies high-value targets
- Lateral movement techniques:
- Pass-the-hash attacks
- RDP session hopping
- Credential harvesting from memory
- Payload Delivery
- Malware deployment through:
- Clipboard hijacking
- Drive sharing abuse
- Fake update mechanisms
- Persistent backdoors:
- Scheduled tasks
- Registry modifications
- Service installation
- Cleanup and Evasion
- Log manipulation to remove traces
- Timestamp modification
- Use of legitimate Windows utilities (living-off-the-land)
- Traffic blending with normal RDP patterns


