Sauron Locker 2024
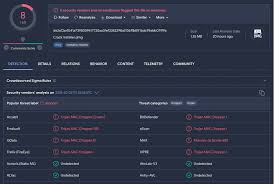
Sauron Locker 2024 represents a significant leap in ransomware sophistication, combining advanced encryption methods with stealthy infiltration techniques. This malware variant targets both individual users and enterprise networks, employing a double-extortion model that encrypts files while exfiltrating sensitive data. Its modular design and polymorphic code make it particularly resistant to traditional security measures, posing a serious challenge to cybersecurity professionals worldwide.
Download Link 1
Download Link 2
Download Link 3
Download Link 4

What is Sauron Locker 2024?
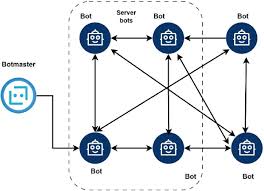
Sauron Locker 2024 is a ransomware-as-a-service (RaaS) platform distributed through underground cybercrime channels. Unlike conventional ransomware, it incorporates military-grade encryption algorithms, lateral movement capabilities, and automated data exfiltration functions. The malware operates on a subscription model, allowing even inexperienced hackers to deploy sophisticated attacks while the developers take a percentage of ransom payments.
Detailed Features of Sauron Locker 2024
| Feature Category | Technical Specifications |
|---|---|
| Encryption Mechanism | Uses ChaCha20 + RSA-4096 hybrid encryption with unique keys per victim |
| Infection Vector | Spreads via phishing emails, RDP brute-forcing, and exploit kits |
| Lateral Movement | Employs Mimikatz for credential dumping and PsExec for network propagation |
| Data Exfiltration | Automatically uploads files to attacker-controlled cloud storage before encryption |
| Anti-Analysis | Implements process hollowing, API unhooking, and VM/sandbox detection |
| Persistence | Creates scheduled tasks, registry modifications, and hidden admin accounts |
| Evasion Techniques | Uses reflective DLL loading and encrypted payloads to bypass signature detection |
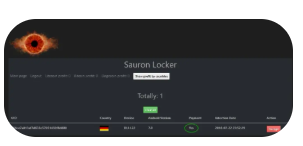
| Payment Portal | Includes a Tor-based negotiation panel with live chat support |
| Target Selection | Features configurable target lists (file extensions, network shares) |
| Self-Destruction | Leaves no traces after execution through careful log cleaning |
Why Do Hackers Use Sauron Locker 2024?
Profitability – Double extortion model (encryption + data leak) increases payment likelihood
Low Technical Barrier – RaaS model enables less skilled hackers to launch sophisticated attacks
High Success Rate – Advanced evasion techniques bypass most traditional security solutions
Scalability – Can simultaneously target multiple organizations through automated propagation
Anonymity – Built-in Tor communication and cryptocurrency payments obscure money trails