SQLi Dork Scanner with Dork list 2025
In modern cyberattacks, SQLi Dork Scanner) remains one of the most prevalent and dangerous vulnerabilities, allowing attackers to manipulate databases and extract sensitive information. Attackers often use specialized tools to automate the discovery of vulnerable websites. One such method involves leveraging search engine dorks—carefully crafted search queries that identify websites with potential security flaws. The SQLi Dork Scanner with Dork List 2025 is a tool designed to streamline this process, enabling both security researchers and malicious actors to locate and assess websites susceptible to SQL injection quickly. While ethical penetration testers use such tools to secure systems, cybercriminals exploit them to identify targets for data breaches.
What Is SQLi Dork Scanner and How Is It Used?
This software is an automated scanner that combines a curated list of up-to-date search engine dorks (as of 2025) with SQL injection detection capabilities. Its primary function is to identify websites that may be vulnerable to SQL injection by querying search engines and then testing the returned URLs for common injection flaws. Security professionals may use it during vulnerability assessments to patch weaknesses, while attackers misuse it to find exploitable targets. The tool typically includes features such as customizable dork lists, proxy support to evade detection, and various scanning techniques to circumvent basic security measures.
Download Link 1
Download Link 2
Download Link 3
Key Features of SQLi Dork Scanner
| Feature | Description |
| Preloaded Dork List (2025) | A frequently updated collection of search queries to find potentially vulnerable sites. |
| Automated Scanning | Tests identified URLS with SQL injection vulnerabilities without requiring manual intervention. |
| Proxy & Tor Support | Allows anonymous scanning by routing requests through proxies or the Tor network. |
| Custom Payload Injection | Supports user-defined payloads for testing various SQL injection (SQLi) attack vectors. |
| Multi-Threading | Speeds up scanning by processing multiple targets simultaneously. |
| Result Export | Saves findings in formats like CSV or TXT for further analysis. |
| WAF Bypass Techniques | Implements methods to evade basic Web Application Firewall (WAF) protections. |
How the Software Works
1. Dork-Based Target Discovery
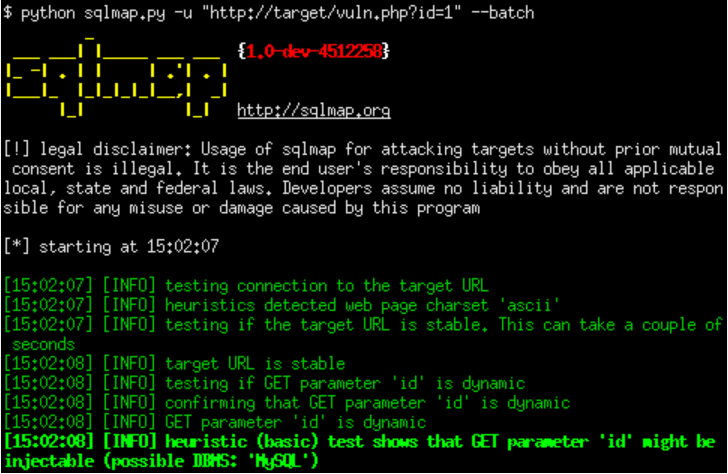
The tool begins by utilising predefined or user-submitted dorks to query search engines such as Google, Bing, or DuckDuckGo. These dorks are designed to locate websites with parameters that may be vulnerable to SQL injection. The scanner extracts URLS from search results and compiles a target list.
2. Vulnerability Scanning
Once targets are identified, the software sends crafted SQL injection payloads to input fields, such as URL parameters and login forms. Common techniques include:
- Boolean-Based Testing: Sends conditional queries to check for database errors or unexpected behaviour.
- Time-Based Testing: Uses delayed responses to confirm vulnerabilities.
- Error-Based Detection: Analyzes database error messages to determine exploitability.
3. Payload Delivery & Exploitation
If a vulnerability is detected, the tool may execute additional payloads to extract database information, such as table names or user credentials. Some advanced versions include automated exploitation modules that dump data directly from the database.
4. Evasion & Anonymity
To avoid detection, the scanner can:
- Rotate user agents and IPS (via proxies/Tor).
- Use encoded or obfuscated payloads to bypass web application firewalls (WAFS).
- Throttle requests to prevent rate-limiting or blocklisting.
5. Reporting & Output
Finally, the tool generates a report that lists vulnerable URLS, injected payloads, and, in some cases, extracted data. This allows the user to either secure the flaws or proceed with further exploitation.
By automating the discovery and verification of SQLi vulnerabilities, this tool significantly reduces the time required for both defensive and offensive security operations. However, its misuse poses a serious threat to unprotected web applications.
![Work With Dorks [DORK’s Generator]-Dork Generator](https://blackhatus.com/wp-content/uploads/2025/07/Work-With-Dorks-DORKs-Generator-Dork-Generator-1.png)