SQLi Toolkit 2025
In today’s rapidly evolving cybersecurity landscape, automated exploitation tools have become a significant concern for defenders. Among these, SQLi Toolkit 2025 has emerged as a hazardous tool due to its ability to efficiently identify and exploit SQL injection (SQLi) vulnerabilities. SQLi remains one of the most prevalent attack vectors, enabling attackers to bypass authentication, steal sensitive data, or even take complete control of vulnerable databases. Unfortunately, this toolkit automates much of the exploitation process, lowering the barrier to entry for less-skilled attackers and significantly increasing the frequency of SQLi-based breaches.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
Primarily, this software functions as a specialized penetration testing tool designed to detect and exploit SQL injection flaws in web applications. While ethical security researchers may use it for legitimate vulnerability assessments, cybercriminals frequently weaponise it due to its effectiveness and ease of use. Equipped with features such as automated scanning, payload generation, and database fingerprinting, the toolkit enables attackers to execute malicious commands, extract data, and escalate privileges with minimal manual intervention. Consequently, it has become a favoured tool in both red-team exercises and real-world cyberattacks.
Key Features of the SQLi Toolkit 2025
The following table outlines the core functionalities that make this tool particularly dangerous:
| Feature | Description |
|---|---|
| Automated Scanning | Systematically identifies SQLi vulnerabilities in target URLs or input forms. |
| Payload Generation | Dynamically crafts customized SQL queries to evade security filters. |
| Database Fingerprinting | Accurately detects the database type (e.g., Mysql, Postgresql) for precise exploitation. |
| Data Exfiltration | Efficiently extracts sensitive data, including credentials and financial records. |
| Blind SQLi Support | Exploits vulnerabilities where direct feedback is unavailable (e.g., time-based or boolean-based attacks). |
| Bypass Techniques | Implements obfuscation and encoding methods to circumvent web application firewalls (WAFS). |
How the SQLi Toolkit 2025 Works
To better understand how this tool operates, let’s examine its step-by-step workflow, which combines reconnaissance, exploitation, and post-exploitation techniques.
1. Target Identification
First, the tool scans a given URL or input field to locate potential injection points, such as login forms, search bars, or API endpoints. During this phase, it sends harmless probes to assess whether the application behaves in a way that suggests an SQLi vulnerability—for instance, by triggering database errors or causing unexpected delays in response times.
2. Vulnerability Confirmation
Once a potential flaw is detected, the software sends carefully crafted SQL queries to confirm the vulnerability. For example, it might inject a single quote, generate a database error or use a boolean-based payload to test for logical weaknesses. If the application responds as expected, the tool proceeds to the exploitation phase.
3. Exploitation & Payload Delivery
After confirming the vulnerability, the toolkit generates malicious SQLi Toolkit 2025 payloads tailored to the specific database backend. These payloads typically fall into three categories:
- Union-Based Attacks – Combines legitimate queries with malicious ones to extract hidden data.
- Time-Based Blind SQLi – Uses delayed responses to infer information indirectly.
- Out-of-Band Exploitation – Leverages DNS or HTTP requests to exfiltrate data when direct retrieval is blocked.
4. Data Extraction & Post-Exploitation
At this stage, the tool automates the extraction of database contents, including tables, columns, and sensitive records. In more advanced cases, it may even escalate privileges or execute system commands on the underlying server, especially if the database is misconfigured.
5. Evasion Techniques
To avoid detection, the software employs various obfuscation methods, such as:
- Hexadecimal encoding – Converts malicious queries into hex format to bypass filters.
- Comment insertion – Adds unnecessary comments to break up suspicious SQL syntax.
Case-switching – Alternates between uppercase and lowercase letters to evade signature-based detection.
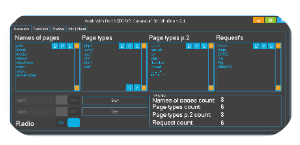
![Work With Dorks [DORK’s Generator]-Dork Generator](https://blackhatus.com/wp-content/uploads/2025/07/Work-With-Dorks-DORKs-Generator-Dork-Generator-1.png)