Penetration testing software
Elevate Your Cyber Defenses with Webmail and SMTP Bruter 2026 Tool
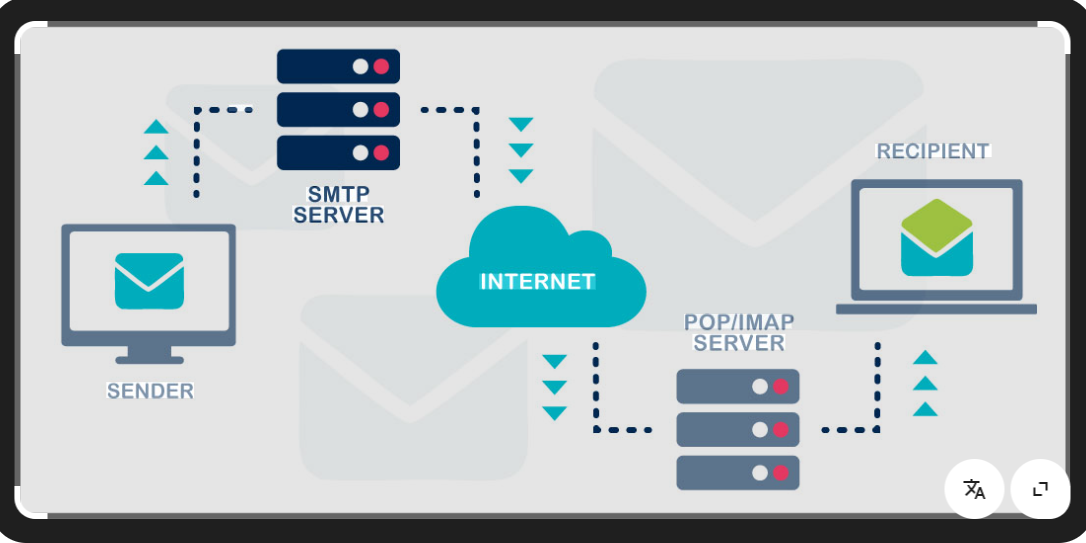
Short Intro: Explore the Webmail and SMTP Bruter 2026, a premier cybersecurity solution crafted for simulating brute-force exploits on email systems during penetration testing. Its core mission is to help organizations fortify their webmail and SMTP defenses by pinpointing exploitable flaws. The unique selling point lies in its AI-enhanced pattern recognition, which predicts and counters […]
Advanced RDP Bruter and Scanner 2026: Boost Your Cyber Defense Arsenal
Short Intro: Introducing the Slayer RDP Scanner and Bruter 2026, a powerful cybersecurity solution tailored for auditing RDP (Remote Desktop Protocol) environments through comprehensive scanning and brute-force attacks. It serves to fortify defenses against unauthorized remote access by pinpointing exploitable RDP flaws. The standout USP is its adaptive intelligence that learns from failed attempts to […]
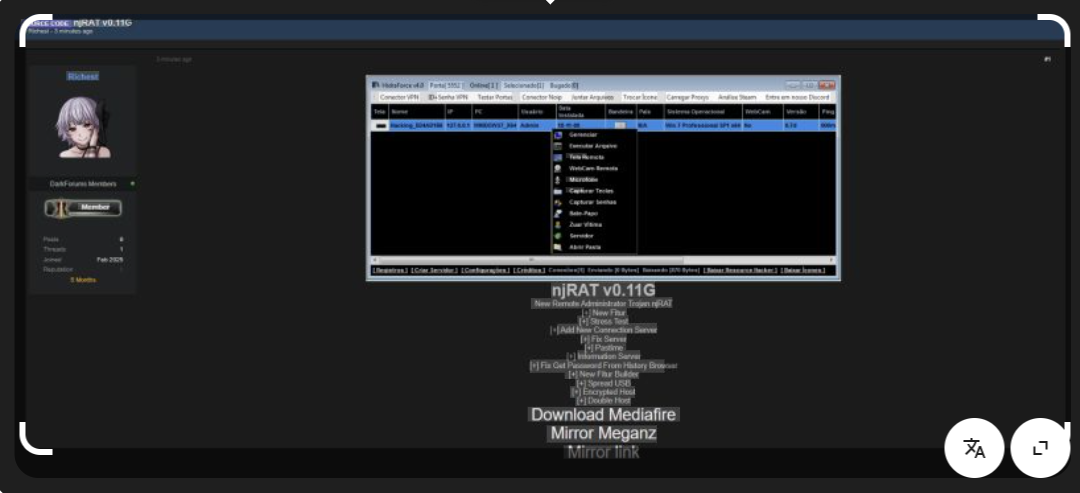
njRAT v0.11g Secure Remote Access in Cybersecurity for 2026
Short Intro: njRAT v0.11g stands out as a cutting-edge remote access tool tailored for cybersecurity experts aiming to fortify defenses through rigorous testing. It serves to emulate hacker techniques safely, identifying weaknesses before real attacks occur. What sets it apart is its user-friendly interface combined with stealthy operation, making it indispensable for professionals tackling 2026’s […]
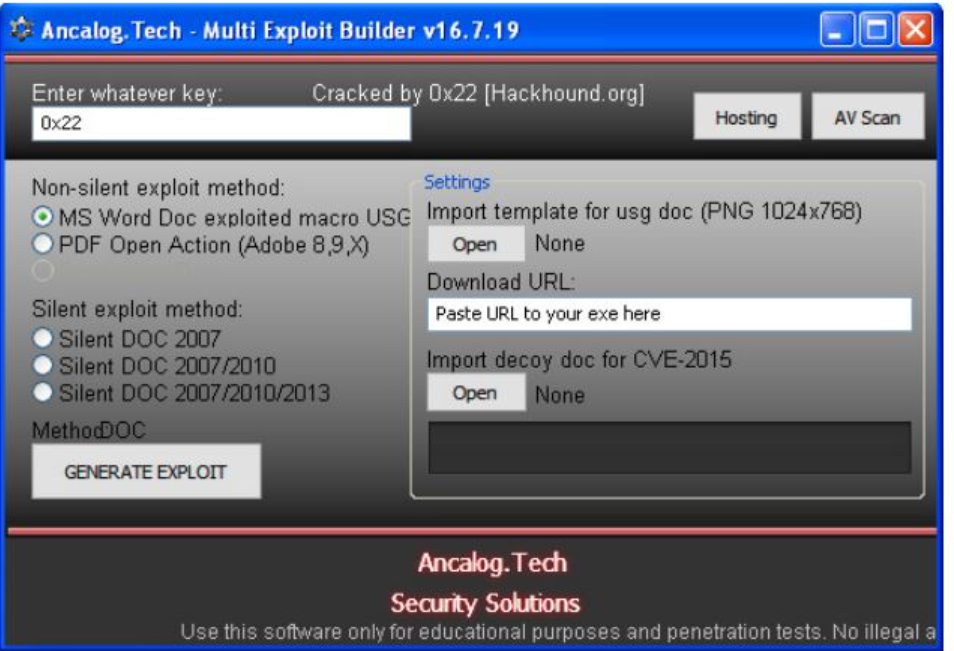
Ancalog Exploit Builder 2026 The Ultimate Penetration Testing Tool
Short Intro: Ancalog Exploit Builder 2026 is a cutting-edge cybersecurity tool designed for ethical hackers and security professionals to create custom exploits for testing vulnerabilities. Its purpose is to streamline exploit development, enabling faster identification of weaknesses in systems. The key USP lies in its AI-driven automation, which reduces manual coding by up to 70%, […]
Multi Account Cracker 2026 Cracked
Short Intro: Introducing Multi Account Cracker 2026 Cracked, a robust cybersecurity tool engineered for professionals to probe and expose weaknesses in multiple account setups. It serves the critical purpose of enhancing digital security by simulating unauthorized access attempts in controlled environments. What sets it apart is its unparalleled efficiency in cracking diverse account types, reducing […]
RDP Brute 2026 Advanced Cybersecurity Solution
Short Intro: RDP Brute 2026 stands out as a powerful cybersecurity utility tailored for professionals conducting Remote Desktop Protocol penetration tests. It systematically attempts to log in with credentials to uncover exploitable weaknesses in RDP setups. What sets it apart is its adaptive intelligence that evolves attack strategies based on real-time feedback, ensuring thorough and […]