Twilight Stealer 2024
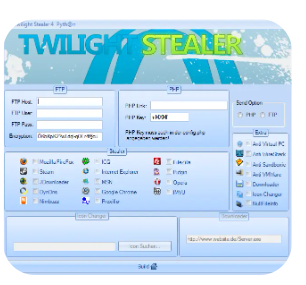
Twilight Stealer 2024 is a sophisticated information-stealing malware designed to extract sensitive data from compromised systems. Unlike traditional stealers, it employs advanced evasion techniques, targeting browsers, cryptocurrency wallets, FTP clients, and more. Its modular architecture and regular updates make it a persistent threat in the cybersecurity landscape.

What is Twilight Stealer 2024
Twilight Stealer 2024 is a malware-as-a-service (MaaS) tool distributed on underground forums, allowing hackers to steal credentials, financial data, and system information. It operates stealthily, bypassing antivirus detection and exfiltrating data to attacker-controlled servers. Security researchers classify it as a high-risk threat due to its adaptability and widespread targeting of individuals and organizations.
Detailed Features of Twilight Stealer 2024
| Feature Category | Description |
|---|---|
| Data Theft Capabilities | Harvests saved passwords, cookies, credit card details, and autofill data from browsers (Chrome, Firefox, Edge). |
| Cryptocurrency Targeting | Extracts private keys and seed phrases from wallets (Metamask, Exodus, Electrum, etc.). |
| System Information | Collects OS details, hardware specs, installed software, and network configurations. |
| Anti-Detection | Uses obfuscation, code injection, and VM/sandbox evasion to avoid detection. |
| Persistence Mechanisms | Establishes registry modifications, scheduled tasks, and hidden startup entries. |
| Exfiltration Methods | Sends stolen data via encrypted channels (Telegram, Discord, or C2 servers). |
| Additional Modules | Supports keylogging, screenshot capture, and clipboard monitoring for real-time data theft. |
| Customization | Buyers can configure target applications, evasion techniques, and C2 settings. |
Why Do Hackers Use Twilight Stealer 2024?
High Success Rate – Advanced evasion techniques bypass security software.
Wide Target Range – Steals from browsers, wallets, FTP clients, and more.
Easy Deployment – Sold as a service with user-friendly panels for less technical hackers.
Profit Potential – Stolen data is monetized on dark web markets or used in further attacks.
Regular Updates – Developers frequently release patches to counter security fixes.


