WISH ACCOUNT CHECKER 2025
The rise of e-commerce platforms has led to a corresponding surge in cybercriminal tools designed to exploit these digital marketplaces. Among these threats, automated WISH ACCOUNT CHECKER 2025 have become particularly prevalent in 2025, allowing attackers to systematically test stolen credentials against retail platforms. These tools serve as the first stage in sophisticated fraud chains, allowing cybercriminals to identify active accounts with stored payment methods, loyalty points, or other monetizable assets. Their efficiency and scalability make them a favoured tool in credential-stuffing attacks, contributing to billions of dollars in e-commerce fraud losses annually while presenting unique detection challenges due to their ability to blend in with legitimate user traffic.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
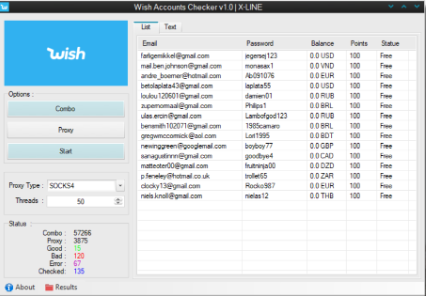
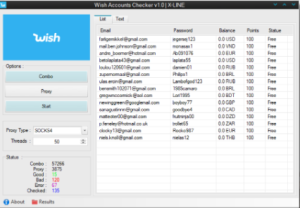
credentials against a popular e-commerce platform. It automates the account verification process by systematically attempting logins and analyzing responses to identify active accounts with valuable assets. Cybercriminals typically use the software to filter massive credential dumps (often obtained from third-party breaches) to identify accounts worth exploiting. Successful verifications are then either used directly for fraudulent purchases, sold on dark web marketplaces, or leveraged in more sophisticated account takeover schemes. The tool’s effectiveness stems from its platform-specific adaptations, which enable it to navigate the unique authentication flows and security measures employed by the target e-commerce site.
Key Features of WISH ACCOUNT CHECKER 2025
| Feature | Description |
| Bulk Credential Processing | Handles thousands of credential pairs per hour with configurable threading |
| Platform-specific Logic | Built-in understanding of the target site’s authentication workflow |
| Proxy Rotation System | Automatic IP switching to evade rate limits and geographic restrictions |
| Asset Detection | Identifies stored payment methods, gift card balances, and loyalty points |
| CAPTCHA Bypass | Integrates with solving services and AI recognition for automated challenges |
| Session Hijacking | Capability to maintain authenticated sessions for later exploitation |
| Detailed Reporting | Exports valid accounts with associated metadata (balance, payment methods etc.) |
| Fraud Scoring | Ranks accounts by potential value based on detectable assets |
How the WISH ACCOUNT CHECKER 2025 Works
The tool operates through a multi-phase attack process optimized for efficiency and stealth:
- Credential Preparation and Input
- Accepts credential lists in various formats (email: password, username: password)
- Normalizes input data to match platform requirements (case sensitivity, formatting)
- Optional pre-processing to apply common password mutations (seasonal variations, incremental numbers)
- Authentication Attempt
- Simulates legitimate login sequences, including:
- Initial page requests with proper headers and cookies
- Form submissions with accurate field mappings
- Handling of platform-specific security tokens
- Manages the complete authentication flo,w including:
- Multi-step login processes
- Security challenge responses
- Error condition handling
- Simulates legitimate login sequences, including:
- Response Analysis
- Interprets server responses to distinguish between:
- Invalid credentials
- Locked/temporarily restricted accounts
- Successful authentications
- For successful logins, performs light reconnaissance to:
- Check available payment methods
- Verify account balances (cash/gift cards)
- Identify saved shipping addresses
- Interprets server responses to distinguish between:
- Evasion Techniques
- Implements sophisticated traffic shaping:
- Randomized delays between attempts (300- 5000ms)
- Naturalistic mouse movement simulation
- Varied browsing patterns
- IP rotation through:
- Residential proxy networks
- Cloud hosting providers
- TOR exit nodes (for certain operations)
- Implements sophisticated traffic shaping:
- Post-Verification Processing
- Categorizes valid accounts by:
- Available payment methods
- Purchase history patterns
- Account age and activity level
- Formats output for various exploitation paths:
- Direct fraudulent purchasing
- Account resale packages
- A phishing campaign targeting
- Categorizes valid accounts by:
- Payload Delivery (Optional)
- For high-value accounts, we may deploy:
- Payment method additions
- Address book modifications
- Subscription changes
- Maintains persistent access through:
- Email forwarding rules
- Password reset manipulations
- Session token theft
- For high-value accounts, we may deploy:


