WordPress All in One Bruteforce 2025
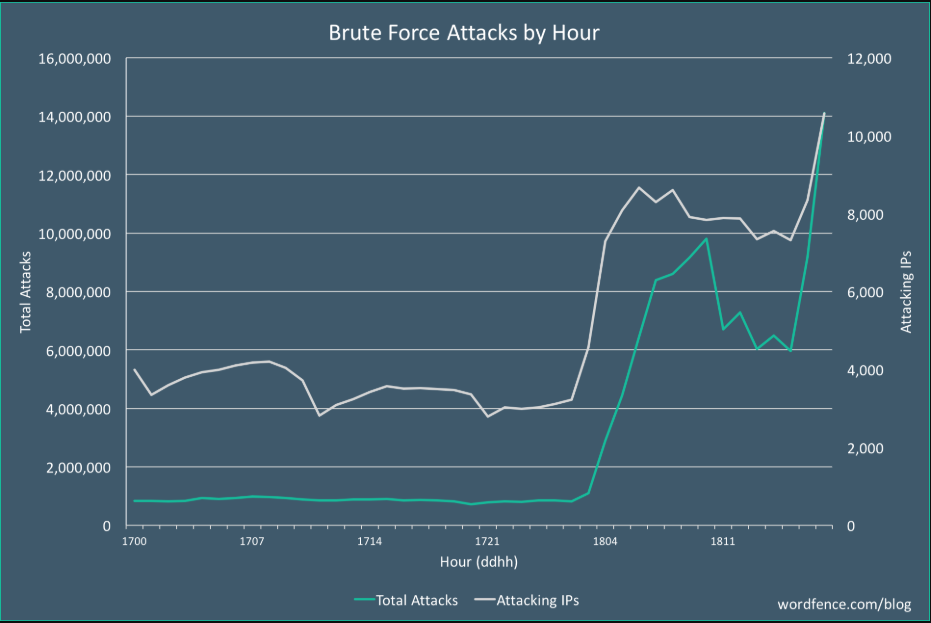
Cyberattacks targeting content management systems (CMS) like WordPress remain a significant threat in 2025, with brute-force attacks being one of the most common attack vectors. These attacks exploit weak credentials, misconfigured security settings, or outdated plugins to gain unauthorized access. Attackers often leverage automated tools to systematically guess login credentials, allowing them to hijack websites, deploy malware, or steal sensitive data. Given WordPress All in One Bruteforce, designed for brute-forcing its authentication systems, continues to evolve, posing a persistent challenge for cybersecurity professionals.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
This software is a specialized tool designed to automate brute-force attacks against WordPress websites. It systematically tests username and password combinations to exploit weak authentication security. While penetration testers may use such tools for vulnerability assessments, malicious actors frequently deploy them to compromise websites for unauthorized access, data theft, or further exploitation. The software typically supports multi-threaded attacks, proxy integration to evade detection, and customizable wordlists to improve success rates.
Key Features
| Feature | Description |
|---|---|
| Multi-threaded Attacks | Enables simultaneous login attempts for faster credential testing. |
| Proxy Support | Routes traffic through proxies to hide the attacker’s IP address. |
| Custom Wordlists | Allows users to import or modify password lists for targeted attacks. |
| User Enumeration | Identifies valid usernames before launching password attacks. |
| Session Management | Resumes interrupted attacks without starting from scratch. |
| Stealth Mode | Slows down requests to evade rate-limiting or security plugins. |
How WordPress All in One Bruteforce Works
The software operates by systematically attempting to log in to a WordPress site using a list of potential credentials. Below is a breakdown of its functionality:
Target Identification
The attacker inputs the target WordPress login page URL (typically/wp-login.php). The software may first verify the site’s accessibility and WordPress installation.User Enumeration (Optional)
If enabled, the tool identifies valid usernames by exploiting WordPress’s default behavior, such as analyzing error messages or querying author archives.Brute-Force Execution
Using a predefined or custom wordlist, the software sends HTTP POST requests with different username-password combinations. Multi-threading allows it to test hundreds of credentials per minute.Evasion Techniques
To avoid detection, the tool may:Rotate IP addresses via proxies or VPNs.
Randomize user-agent strings.
Delay requests to mimic human behavior.
Payload Delivery
Upon successful login, the attacker gains access to the WordPress dashboard, where they may:Install backdoors via plugins/themes.
Inject malicious scripts.
Deface the website or exfiltrate data.
The software’s efficiency depends on the quality of the wordlist, server security measures (e.g., rate-limiting, CAPTCHA), and whether two-factor authentication (2FA) is enabled. While effective against poorly secured sites, modern defenses like strong passwords, 2FA, and Web Application Firewalls (WAFs) can significantly mitigate such attacks.


