![Work With Dorks [DORK’s Generator]-Dork Generator](https://blackhatus.com/wp-content/uploads/2025/07/Work-With-Dorks-DORKs-Generator-Dork-Generator-1.png)
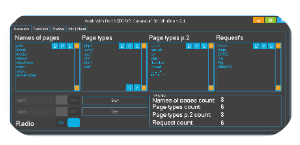
Work With Dorks [DORK’s Generator]-Dork Generator
Work With Dorks is an advanced, automated Google dorking tool designed for cybersecurity professionals, ethical hackers, and penetration testers. It simplifies the discovery of vulnerable websites, exposed databases, and sensitive data by generating and executing accurate search queries. Built for speed and precision, this tool focuses on legal and ethical usage for authorized security research.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
What Is Work With Dorks?
Work With Dorks is a powerful automation utility that utilizes Google’s search operators to reveal hidden vulnerabilities on the web. Compared to manual dorking, it offers:
Pre-configured dork lists covering common vulnerabilities (SQLi, XSS, open directories)
Custom query creation for focused reconnaissance
Batch scanning to analyze numerous websites efficiently
Proxy and TOR integration for anonymous searches
This tool is intended strictly for legitimate security assessments, bug bounty programs, and educational use.
Detailed Features of Work With Dorks
| Feature Category | Description |
|---|---|
| Automated Dork Generation & Execution | Pre-loaded dork database with categories like SQL Injection, exposed admin panels, and sensitive files. |
| Custom query builder supporting Boolean operators, site filters, and filetype targeting (PDF, SQL, LOG). | |
| Advanced Scanning & Enumeration | Bulk URL processing enabling scanning of hundreds of domains per session. |
| Proxy and VPN support to prevent IP bans and ensure anonymity. | |
| Rate-limit bypass using randomized delays to avoid Google CAPTCHAs. | |
| Session management to save and resume large-scale scans. | |
| Output & Reporting | Real-time results filtering by vulnerability type. |
| Export options available in TXT, CSV, or JSON formats. | |
| Integration compatibility with tools like Burp Suite, Metasploit, and sqlmap. | |
| User Experience & Security | Offers both CLI and GUI versions suitable for beginners and experts alike. |
| Educational mode that explains dork syntax and associated risks. | |
| Built-in legal disclaimer warning against unauthorized use. |
Why Use Work With Dorks?
Time-Saving: Automates repetitive and tedious dorking operations.
Comprehensive Coverage: Detects critical OWASP Top 10 vulnerabilities.
Bug Bounty Friendly: Helps find quick wins and reportable vulnerabilities.
Educational: Facilitates learning web security with practical examples.
Customizable: Tailors queries for specialized targets such as APIs and IoT devices.