Malware
Here are various types of malware you can download. Virus, Worm, Trojan, Ransomware, Spyware, Adware, Keylogger, Rootkit and Botnet Malware.
Crypters and Binders Pack
Crypters and Binders Pack is a powerful collection of malware obfuscation and file-binding tools, widely used by cybersecurity researchers, penetration testers, and ethical hackers. It demonstrates how attackers hide malicious code, bind multiple files together, and bypass antivirus detection. By analyzing Crypters and Binders Pack, professionals can learn advanced malware delivery and obfuscation techniques and […]
Project Neptune
Project Neptune is a sophisticated malware tool widely studied by cybersecurity researchers, penetration testers, and ethical hackers. It demonstrates advanced techniques for remote system control, data exfiltration, and stealth operation. By analyzing Project Neptune, professionals can gain insights into modern malware behavior, improve detection strategies, and strengthen system defenses against malicious attacks. Download Link 1 […]
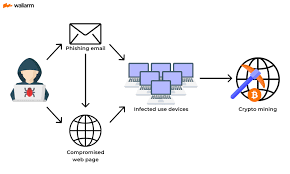
hMinerPTS Bitcoin Miner
hMinerPTS Bitcoin Miner is a cryptocurrency mining malware often studied by cybersecurity researchers, penetration testers, and ethical hackers. It demonstrates how attackers exploit system resources to mine cryptocurrencies without consent. By analyzing hMinerPTS, professionals can understand mining malware behavior, CPU/GPU exploitation techniques, and develop strategies to protect systems from unauthorized crypto-mining activities. Download Link 1 […]
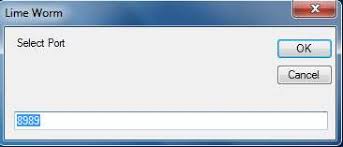
Lime Worm
Lime Worm is a sophisticated malware worm often analyzed by cybersecurity researchers, penetration testers, and ethical hackers. It demonstrates how self-replicating malware spreads across networks, infects systems, and exfiltrates data. By studying Lime Worm, professionals can gain insights into worm propagation techniques, malware persistence, and develop stronger defense mechanisms against network-based attacks. Download Link 1 […]
GalaxyWorkstation powerful toolkit
GalaxyWorkstation is a powerful toolkit often used by cybersecurity researchers, penetration testers, and ethical hackers. It provides a controlled environment for analyzing malware samples such as RATs, keyloggers, and botnets. By using GalaxyWorkstation, professionals can simulate real-world malware attacks, test persistence techniques, and study command-and-control behaviors to strengthen defensive security strategies. Download Link 1 Download […]
Keyloggers Pack
Keyloggers Pack is a collection of powerful keylogging malware samples, often used by cybersecurity researchers, penetration testers, and ethical hackers. This pack provides different types of keyloggers that capture keystrokes, steal credentials, and exfiltrate sensitive data. By studying Keyloggers Pack, professionals can better understand how keylogging malware works and develop stronger defense mechanisms against spyware […]
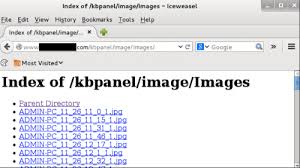
Rats Pack (Remote Access Trojans)
Rats Pack is a powerful collection of Remote Access Trojans (RATs) often studied by cybersecurity researchers, penetration testers, and ethical hackers. It provides a wide variety of RAT samples, each showcasing different techniques used by attackers to remotely control infected systems, steal data, and perform malicious tasks. By analyzing Rats Pack, professionals can gain deeper […]
KeyBase Malware
KeyBase is a stealthy keylogging malware often analyzed by cybersecurity researchers, penetration testers, and ethical hackers. It is designed to record keystrokes, steal sensitive data, and monitor system activities without being detected. By studying KeyBase, professionals can better understand modern keylogger operations and improve defensive mechanisms against spyware and credential theft. Download Link 1 Download […]
Hooker Keylogger v3.0
Hooker Keylogger v3.0 is a powerful keylogging malware often studied by cybersecurity researchers, penetration testers, and ethical hackers. It is designed to secretly record keystrokes, capture sensitive data, and monitor user activity without detection. By analyzing Hooker Keylogger v3.0, professionals can gain valuable insights into keylogging techniques and enhance their defensive strategies against spyware and […]
Loki Bot v2
Loki Bot v2 is a well-known research toolkit for studying password stealers and information-stealing malware. Designed for cybersecurity researchers, penetration testers, and ethical hackers, this tool helps professionals analyze how credential stealers operate, collect sensitive data, and exploit system vulnerabilities. Loki Bot v2 is widely used for malware analysis, training, and security research to improve […]