Trillium Security MultiSploit Tool v6.5.21 Full
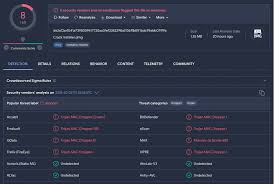
The cybersecurity landscape faces growing threats from sophisticated attack frameworks that bundle multiple exploitation capabilities into a single platform. These advanced Trillium Security MultiSploit lower the barrier to entry for cybercriminals by packaging professional-grade attack vectors with user-friendly interfaces. Particularly dangerous is their ability to automate complex attack chains combining reconnaissance, vulnerability exploitation, and post-compromise […]
Crypto Money Grabber 2025
In the evolving landscape of cybercrime, Crypto Money Grabber 2025 tools designed to steal cryptocurrency have become a significant threat. Among these, specialized malware known as “crypto money grabbers” has emerged as a preferred weapon for attackers targeting digital wallets and exchanges. These tools exploit vulnerabilities in both individual users and systems to siphon funds, […]
SQLi Toolkit 2025
In today’s rapidly evolving cybersecurity landscape, automated exploitation tools have become a significant concern for defenders. Among these, SQLi Toolkit 2025 has emerged as a hazardous tool due to its ability to efficiently identify and exploit SQL injection (SQLi) vulnerabilities. SQLi remains one of the most prevalent attack vectors, enabling attackers to bypass authentication, steal […]
Anubis Crypter FUD 2025
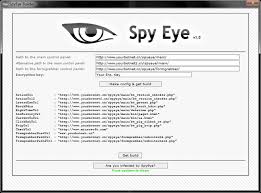
In the arms race between cybercriminals and security professionals, Anubis Crypter FUD 2025 have emerged as a critical weapon for evading detection. The latest iterations of these tools employ increasingly sophisticated methods to bypass even advanced security solutions, enabling malware to operate undetected for extended periods. These evasion capabilities make crypters particularly dangerous in ransomware […]
Echelon Stealer-v5
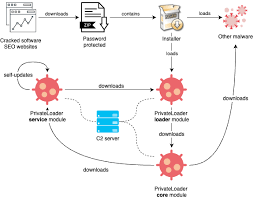
Information stealers have become one of the most pervasive threats in today’s cyber landscape, with sophisticated variants like this Echelon Stealer-v5 playing a significant role in credential theft and financial fraud. Unlike ransomware that announces its presence, these stealthy threats operate silently, harvesting sensitive data that fuels further criminal activity. This particular stealer has gained […]
0 Crypter
Cybercriminals continue to leverage advanced 0 Crypter to bypass security measures, with newer variants becoming more sophisticated in their evasion techniques. These tools play a critical role in modern cyberattacks by enabling malware to remain undetected long enough to compromise systems, exfiltrate data, or establish persistent access. As endpoint detection solutions improve, crypters evolve in […]
ICG Auto Exploiter BoT 2025
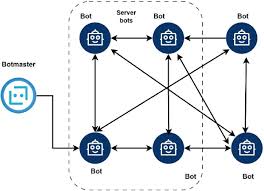
In the evolving landscape of cybersecurity threats, automated exploitation tools have become a significant concern for defenders. Among these, the ICG Auto Exploiter BoT represents a sophisticated example of modern malware designed to identify and exploit vulnerabilities with minimal human intervention. Such tools are frequently employed in large-scale cyberattacks, enabling threat actors to compromise systems, […]
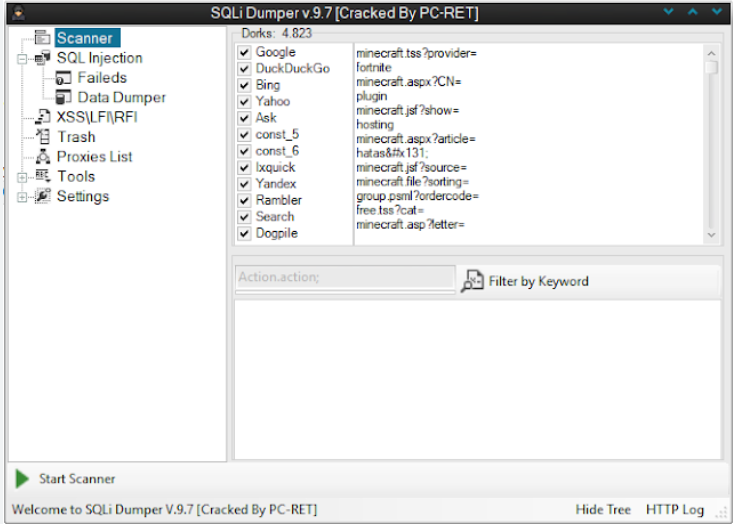
SQLi Dumper 9.7
In the evolving landscape of cybersecurity threats, automated exploitation tools have become a significant concern for organizations worldwide. One such tool, often utilised by malicious actors, is designed to automate the process of identifying and exploiting SQLi Dumper 9.7 vulnerabilities in web applications. These vulnerabilities, if left unpatched, can lead to unauthorized data access, data […]
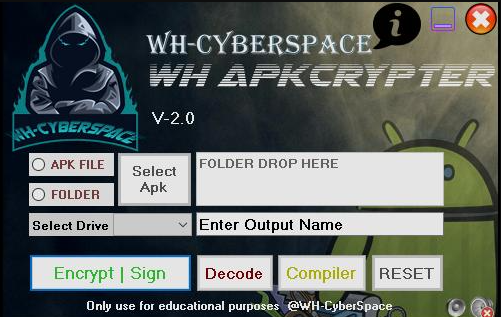
WH ApkCrypter V2
In the evolving landscape of cybersecurity, malicious actors increasingly rely on advanced tools to bypass detection and deploy harmful payloads. One such tool, known for its ability to evade traditional security measures, is the WH ApkCrypter V2. This type of software plays a significant role in modern cyberattacks, particularly in obfuscating malware to avoid analysis […]
Acordx Crypter 2024 Cracked
In today’s cybersecurity landscape, Acordx Crypter 2024 are playing an increasingly significant role in enabling sophisticated cyberattacks. These tools are specifically designed to bypass modern security measures by disguising malicious code, making them a favourite among ransomware operators, data thieves, and other cybercriminals. Cracked or pirated versions of crypters circulating in underground forums further lower […]