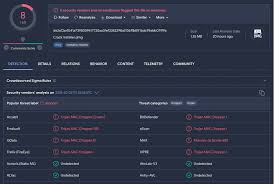
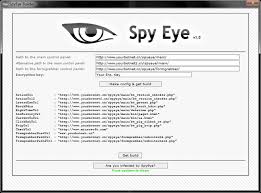
Mirai Eye Rat 2025 Cracked
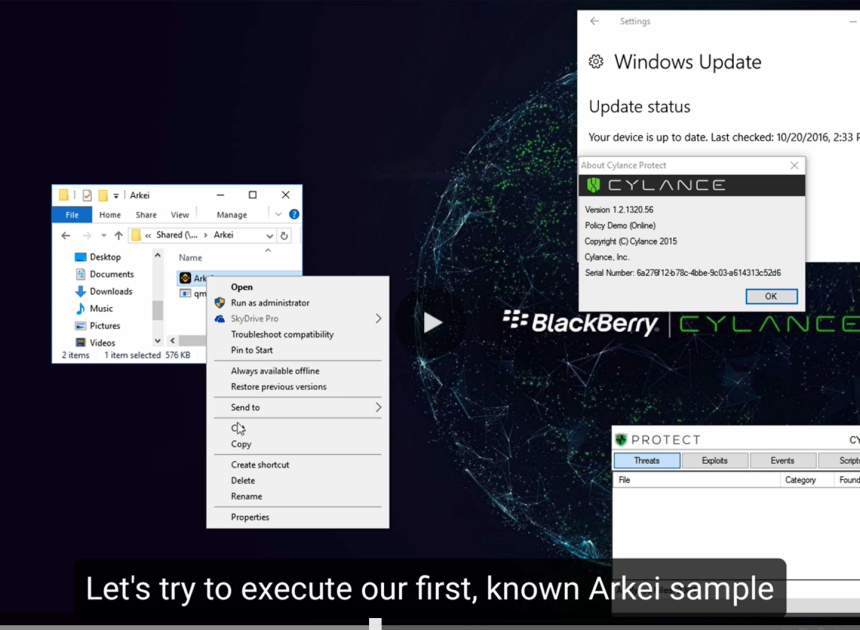
Mirai Eye Rat 2025 has emerged as a dangerous Remote Access Trojan (RAT) frequently deployed in targeted cyberattacks, particularly in espionage and data theft campaigns. Unlike generic malware, Mirai Eye is designed for stealth and persistence, allowing attackers to maintain long-term access to compromised systems. It is commonly used against high-value targets, including government agencies, […]
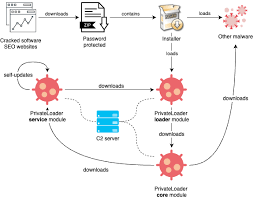
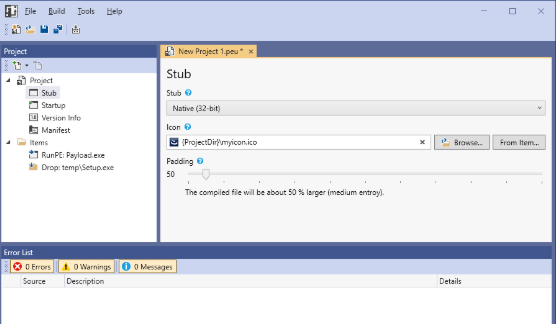
PEUNION Crypter 2024
In the ever-evolving world of cyber threats, PEUNION Crypter 2024 have become a crucial tool for attackers looking to bypass security measures and deliver malicious payloads undetected. These programs specialise in obfuscating and encrypting malware, making it difficult for traditional antivirus solutions to detect and identify them. Modern cyberattacks, including ransomware, banking trojans, and spyware, […]
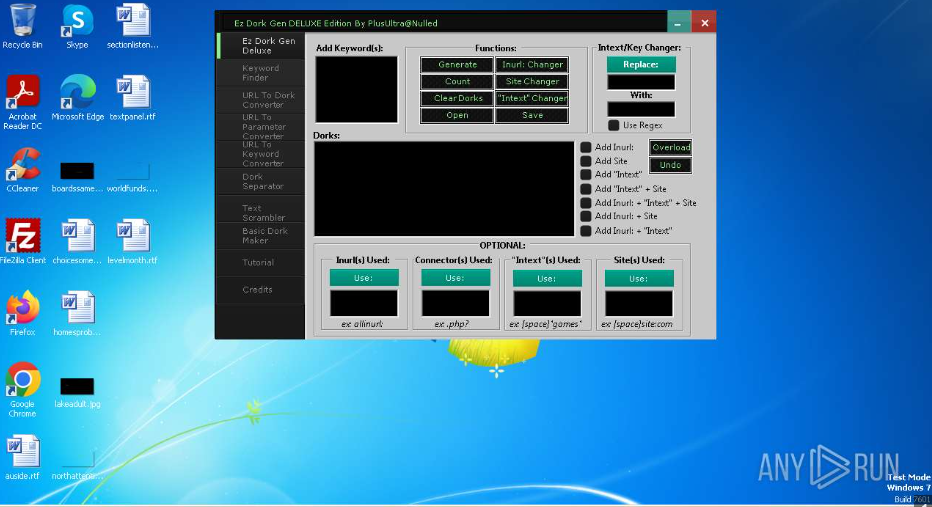
Ez Dork Gen DELUXE Edition 2025
Ez Dork Gen DELUXE also known as Google hacking, is a widely used technique for uncovering hidden vulnerabilities, exposed databases, and misconfigured web applications. Advanced threat generation tools streamline this process by automating the creation of targeted search queries, allowing both attackers and security professionals to identify exploitable targets quickly. While ethical hackers utilize these […]
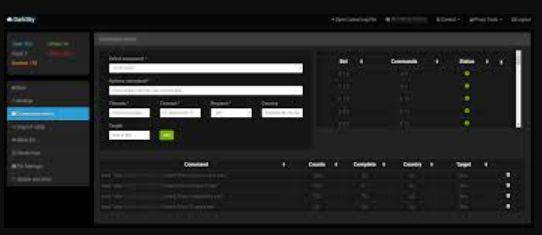
DarkSky DDoS Loader Bot Cracked 2025
DarkSky DDoS Loader Bot (DDoS) attacks persist as a significant threat to the cybersecurity landscape, disrupting services, extorting businesses, and resulting in substantial financial losses. Attackers often rely on powerful botnet tools to amplify their attacks, and one such tool, DarkSky DDoS Loader Bot Cracked 2025, has gained notoriety for its effectiveness and accessibility. This […]
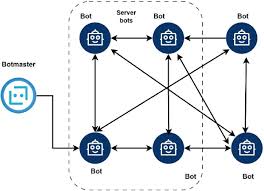
Gold Alduin Botnet 2025
Gold Alduin Botnet 2025 remain one of the most potent threats in cybersecurity, enabling large-scale attacks through networks of compromised devices. One such example is a sophisticated modular botnet frequently used in credential theft, cryptocurrency mining, and distributed denial-of-service (DDoS) attacks. Its ability to evade detection while maintaining persistent control over infected machines makes it […]
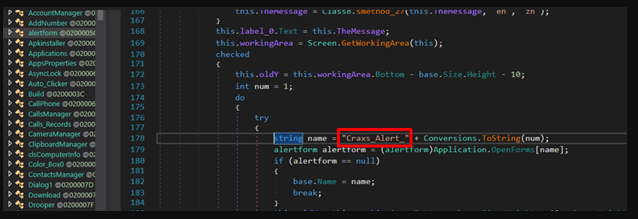
Dangerous Rat-v5 Cracked
Remote Access Trojans (RATs) are among the most dangerous tools in a cybercriminal’s arsenal, enabling stealthy, long-term control over compromised systems. Unlike traditional malware that may simply corrupt files or display ransomware messages, Dangerous Rat-v5 allow attackers to operate undetected, performing espionage, data theft, and even lateral movement across networks. They are frequently used in […]
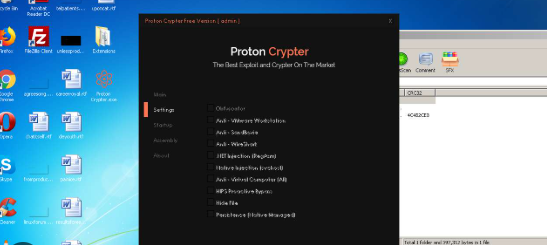
Proton Crypter V 2.0
In the evolving landscape of cybersecurity threats, Proton Crypter V 2.0 has emerged as a critical tool for attackers who aim to evade detection and deploy malicious payloads. These programs are specifically designed to obfuscate and encrypt harmful code, thereby making it extremely difficult for traditional antivirus solutions to identify and block them. Consequently, modern […]
Visual Protector 0.5
In modern cyberattacks, tools like Visual Protector 0.5 play a significant role in bypassing security measures and delivering malicious payloads. These tools are often used by threat actors to evade detection, making them a persistent challenge for cybersecurity professionals. By leveraging obfuscation, encryption, and other evasion techniques, such tools enable malware to infiltrate systems undetected, […]
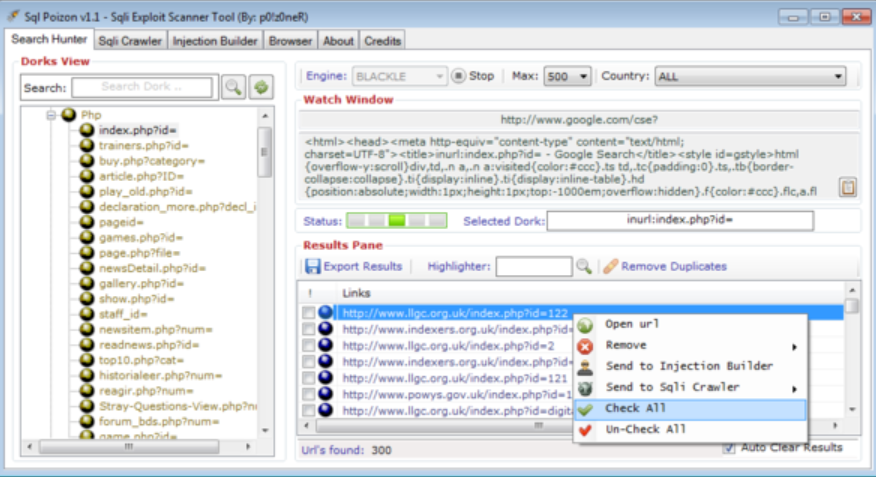
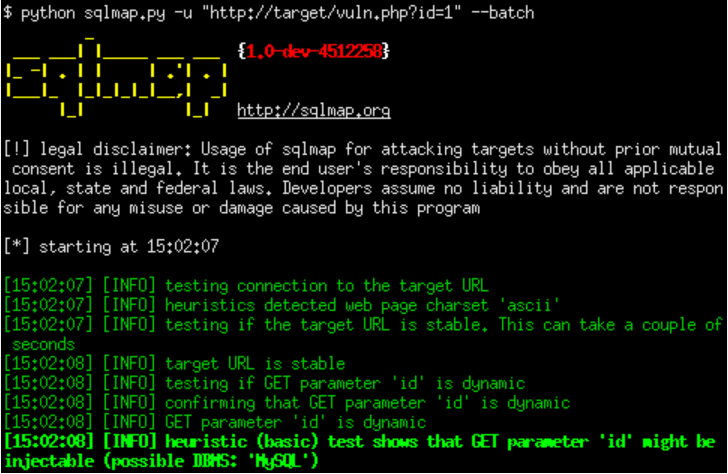
SQLi Dork Scanner with Dork list 2025
In modern cyberattacks, SQLi Dork Scanner) remains one of the most prevalent and dangerous vulnerabilities, allowing attackers to manipulate databases and extract sensitive information. Attackers often use specialized tools to automate the discovery of vulnerable websites. One such method involves leveraging search engine dorks—carefully crafted search queries that identify websites with potential security flaws. The […]
Agent tesla builder-3-2-5-5 cracked
In the ever-evolving world of cyber threats, agent-tesla-builder has become a significant concern for security professionals. These tools allow attackers to create customized malware strains with minimal effort, enabling widespread espionage, data theft, and system compromise. One such example is a well-known Remote Access Trojan (RAT) builder, frequently distributed on underground forums and used in […]