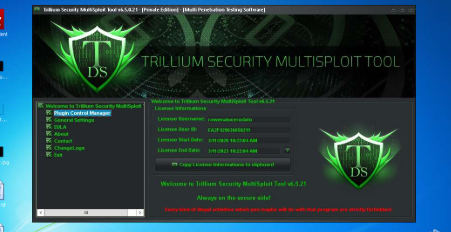
Trillium Security MultiSploit Tool v6.5.21 Full
The cybersecurity landscape faces growing threats from sophisticated attack frameworks that bundle multiple exploitation capabilities into a single platform. These advanced Trillium Security MultiSploit lower the barrier to entry for cybercriminals by packaging professional-grade attack vectors with user-friendly interfaces. Particularly dangerous is their ability to automate complex attack chains combining reconnaissance, vulnerability exploitation, and post-compromise actions. Security teams now encounter these frameworks in everything from targeted intrusions to widespread malware campaigns, where their modular design allows attackers to customise payloads while evading conventional security measures.
Download Link 1
Download Link 2
Download Link 3
Download Link 4
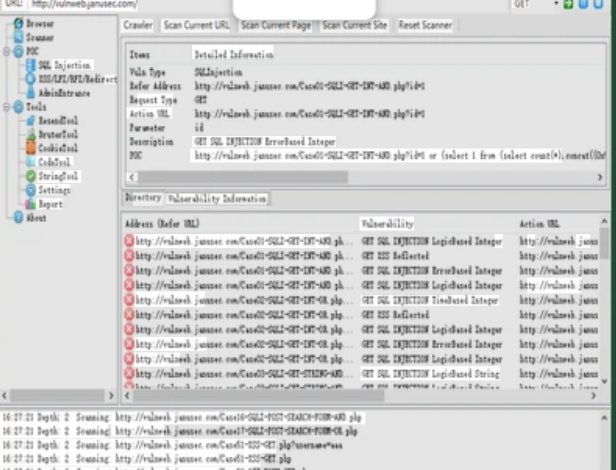
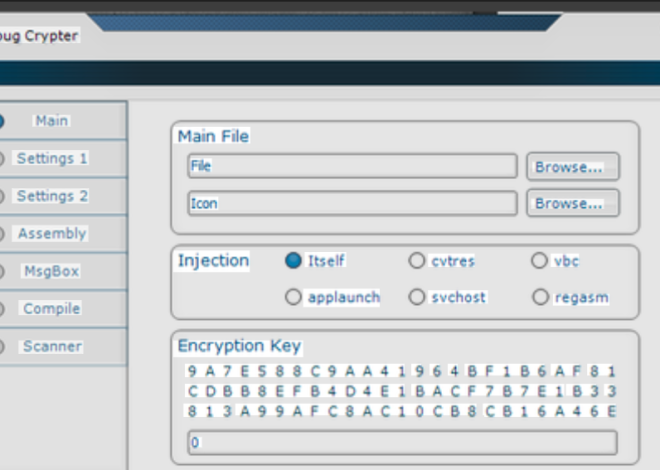
This software represents a comprehensive penetration testing framework that malicious actors have weaponised. It combines multiple exploitation modules with built-in evasion techniques, functioning as an all-in-one platform for network intrusion and system compromise. While initially developed for legitimate security testing, its leaked and cracked versions now circulate in underground markets where cybercriminals use it to deploy ransomware, credential stealers, and remote access trojans. The toolkit’s modular architecture allows attackers to chain together reconnaissance, exploitation, and post-exploitation activities with minimal technical expertise required.
Key Features of Trillium Security MultiSploit
| Feature | Description |
| Multi-Exploit Engine | Bundles 50+ pre-configured exploits for common vulnerabilities |
| Automated Payload Crafting | Generates undetectable malware variants based on the target environment |
| Living-off-the-Land | Leverages legitimate system tools for post-exploitation activities |
| Network Propagation | Includes built-in lateral movement modules for enterprise environments |
| Traffic Obfuscation | Encrypts C2 communications using TLS and custom protocols |
| Anti-Forensics Kit | Automated evidence removal and log manipulation tools |
How Trillium Security MultiSploit Tool v6.5.21 Works
The framework operates through a staged approach that automates sophisticated attack sequences:
- Reconnaissance Phase
- Performs automated network scanning using the integrated Nmap engine
- Fingerprints target systems (OS, services, security products)
- Cross-reference findings with the vulnerability database
- Generates a tailored attack plan based on discovered weaknesses
- Exploitation Phase
- Selects the appropriate exploit module from its database
- Dynamically crafts payload to match target architecture
- Deploys memory corruption or configuration-based attacks
- Uses advanced techniques like:
- Heap grooming for browser-based exploits
- ROP chain construction for bypassing DEP/ASLR
- Timing attacks against network services
- Payload Delivery & Execution
- Implements multiple delivery mechanisms:
- HTML smuggling for browser-based attacks
- SMB relay attacks for network propagation
- WMI subscription for fileless execution
- Deploys final payload using:
- Process Doppelgänging for stealthy execution
- Module stomping to hide in legitimate processes
- Threadless injection to evade behavioural monitoring
- Post-Exploitation Phase
- Establishes persistent access via:
- Hidden scheduled tasks
- WMI event subscriptions
- Service binary path modification
- Executes lateral movement using:
- Pass-the-hash techniques
- Kerberoasting attacks
- RDP hijacking modules
- Deploys cleanup scripts to remove forensic evidence