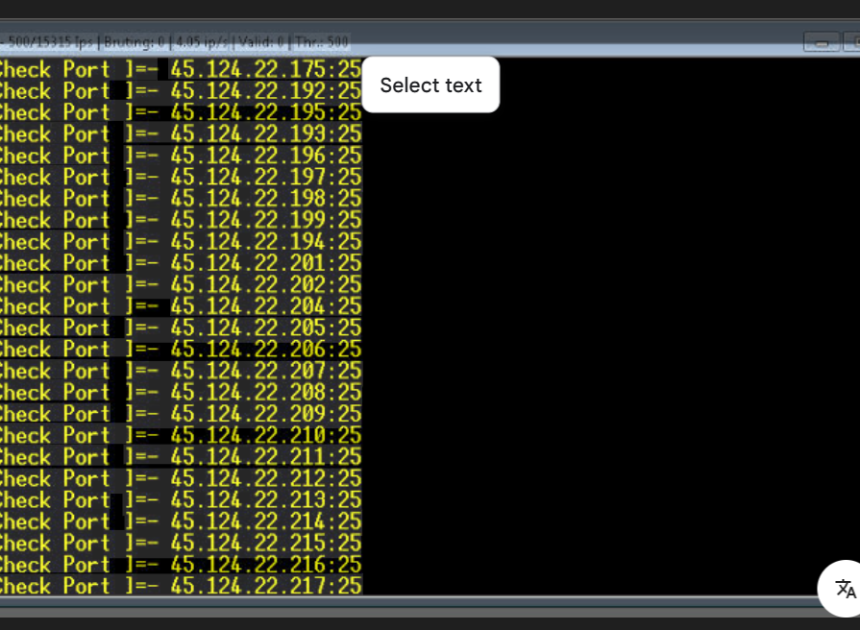
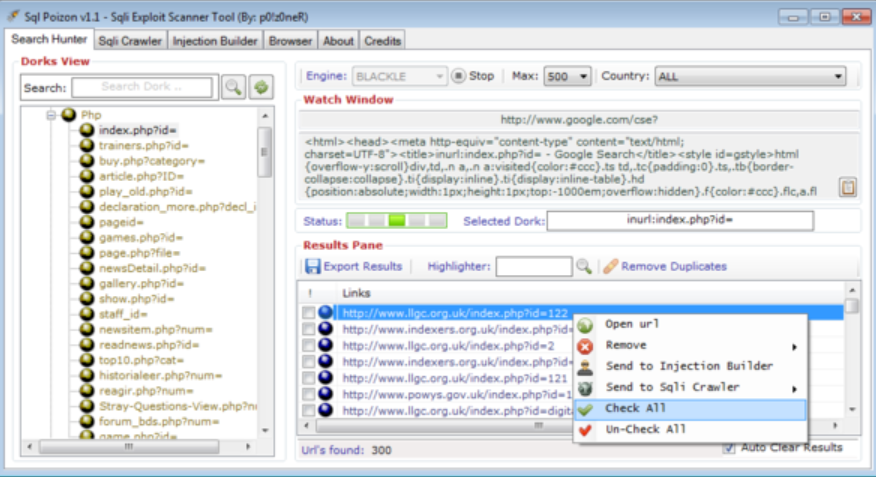
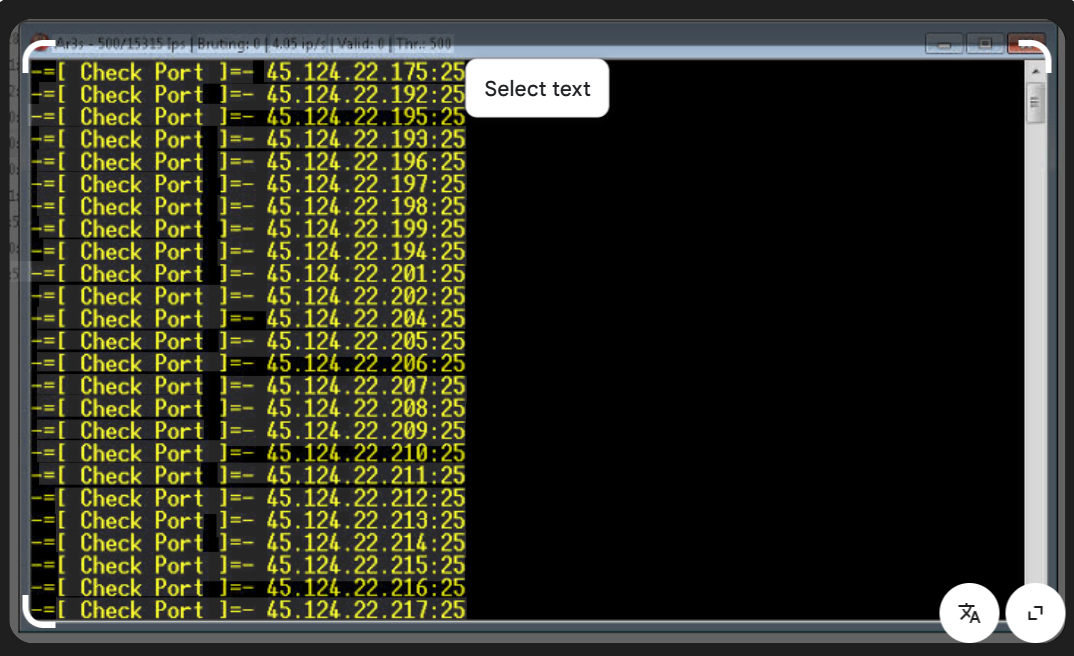
Advanced IP Domain SMTP Scanner and Cracker 2026
Short Intro: Introducing the IP Domain SMTP Scanner and Cracker 2026, an essential cybersecurity utility that scans IP addresses, domains, and SMTP protocols to uncover hidden threats. Its core purpose is to empower IT experts with deep insights into network security gaps, facilitating targeted fixes. What sets it apart is its user-friendly interface combined with […]
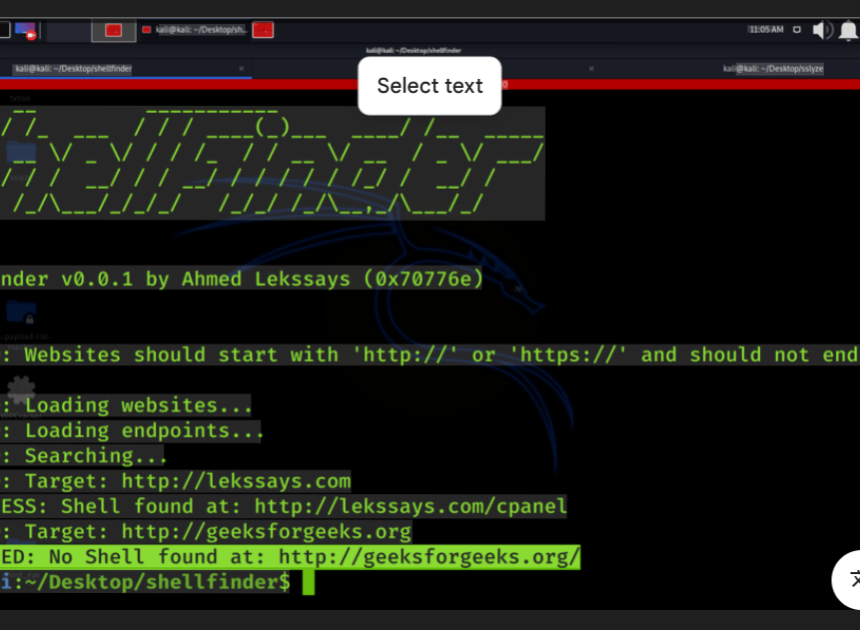
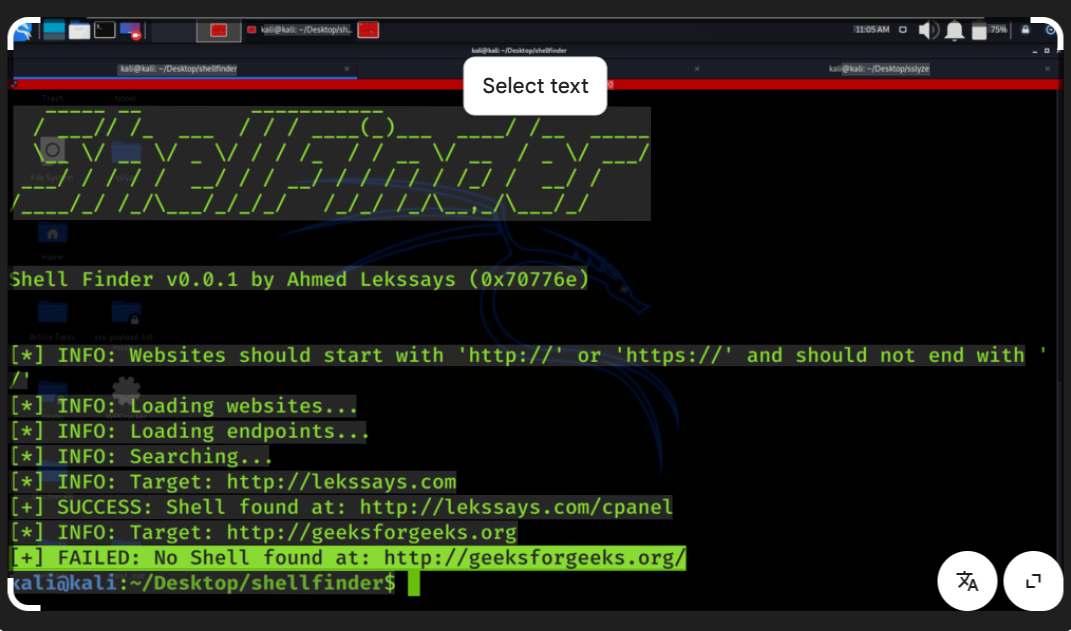
Unlock ShellFinder 2026: Revolutionizing Cybersecurity
Short Intro: ShellFinder 2026 emerges as a powerful cybersecurity tool engineered to locate and assess shell-based vulnerabilities in networks and applications. Its core purpose is to empower security analysts to conduct thorough audits and strengthen defenses against sophisticated cyber threats. What makes it stand out is its adaptive learning capability, which refines detection accuracy over […]
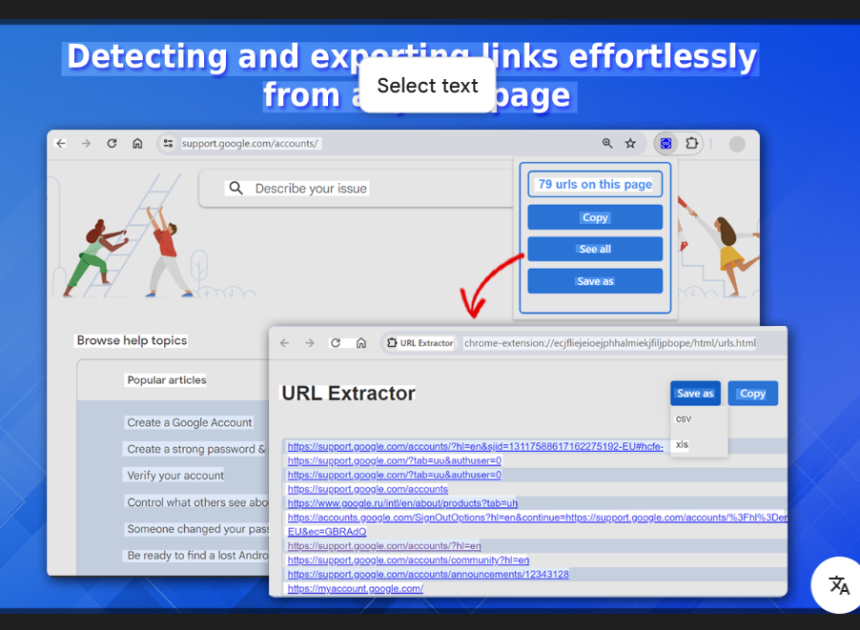
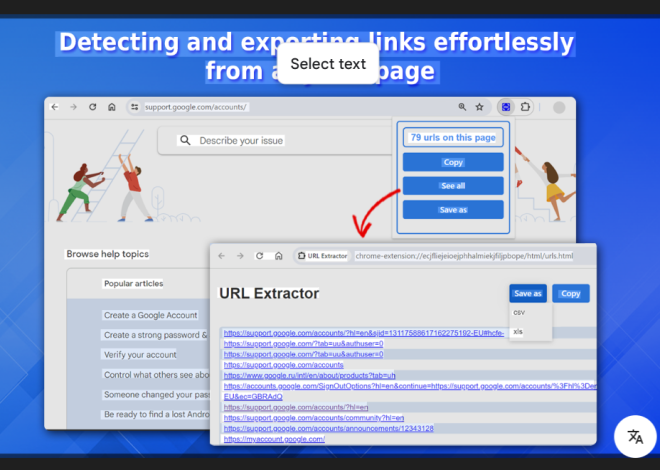
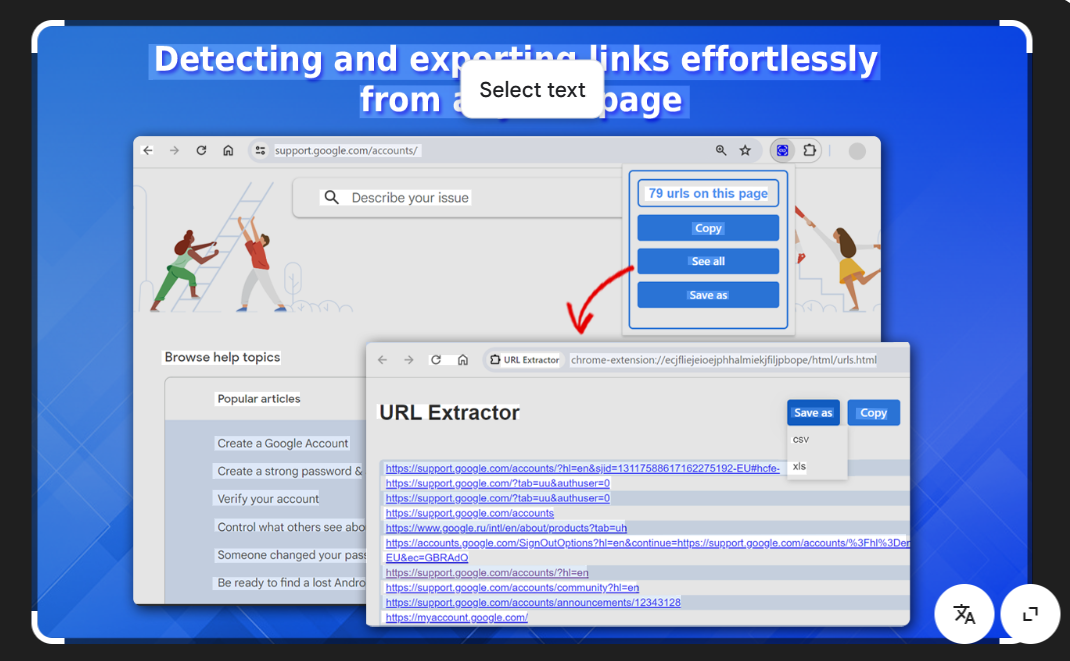
Google’s Hidden URLs with the Ultimate Cybersecurity Extraction Tool
Short Intro: Google URL Extractor 2026 is a powerful cybersecurity tool designed to scrape and extract URLs directly from Google search results for in-depth analysis. It helps security professionals and researchers identify potential threats, track malicious links, and enhance web security audits with high precision. Its unique selling point lies in its advanced AI-driven filtering, […]
SecureNet Shield 2026: Innovative Cybersecurity Tool For Unmatched Digital Resilience
Short Intro: SecureNet Shield 2026 is an essential cybersecurity tool crafted to fortify defenses against the relentless landscape of online dangers. With a focus on simplicity and power, it empowers users to maintain control over their digital environments through intelligent automation. Its standout feature is adaptive learning, which evolves defenses based on user behavior for […]
Master Cybersecurity with Hacker Keylogger 2026
Short Intro: Hacker Keylogger 2026 stands as a robust cybersecurity utility engineered for professionals to surveil and safeguard digital environments. Its core function is to log keystrokes, screen activities, and network interactions to uncover vulnerabilities and mitigate risks. The standout USP is its cloud-based synchronization, enabling real-time data syncing across devices for uninterrupted monitoring. Feature […]
Master Cybersecurity with SMAD SSH Scanner 2026
Short Intro: Introducing SMAD SSH Scanner 2026, a premier cybersecurity tool tailored for identifying and addressing SSH-related security gaps in dynamic environments. Its mission is to provide thorough scans that highlight risks like outdated protocols and weak passwords, safeguarding sensitive data from cyberattacks. Boasting a unique USP of zero-configuration deployment, it delivers enterprise-grade security without […]
Top-Rated Cybersecurity Assessment Tool Multi Hack 2026
Short Intro: Multi Hack 2026 is a powerful cybersecurity tool tailored for professionals conducting ethical hacking and security audits, aimed at exposing and resolving system vulnerabilities. Its mission is to transform passive defenses into proactive strategies by emulating sophisticated cyber attacks. The standout USP is its modular design, allowing users to mix and match features […]
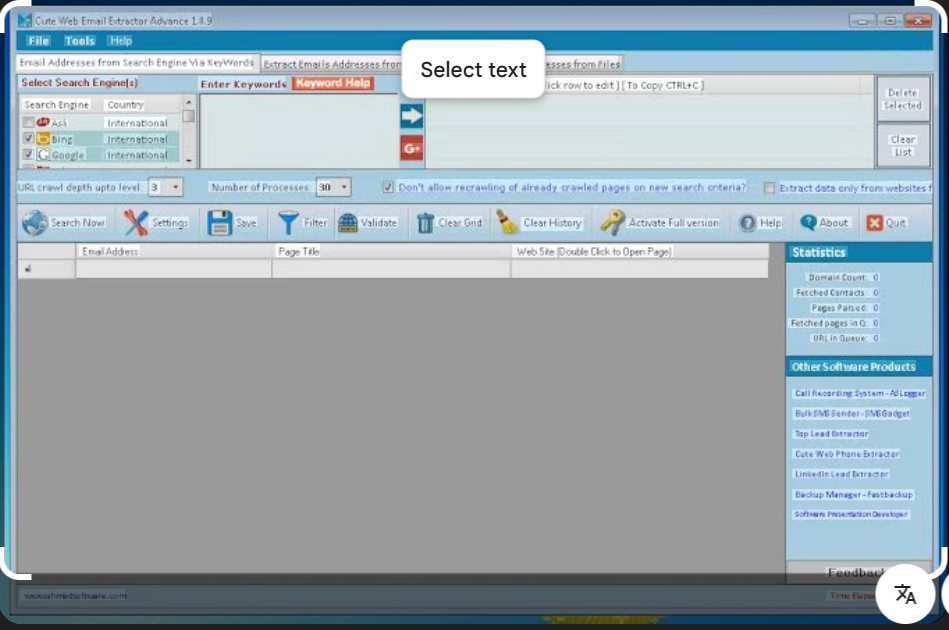
Email Extraction with Cute Web Email Extractor Advance v1.8.9 Cracked
Short Intro: Cute Web Email Extractor Advance v1.8.9 Cracked is an innovative cybersecurity utility focused on automated email retrieval from the web. It aims to simplify data collection for analysts, businesses, and researchers alike. The primary USP is its fully cracked access, unlocking pro-level tools without subscriptions, delivering unmatched value for users. Feature Explanations: In-Depth […]
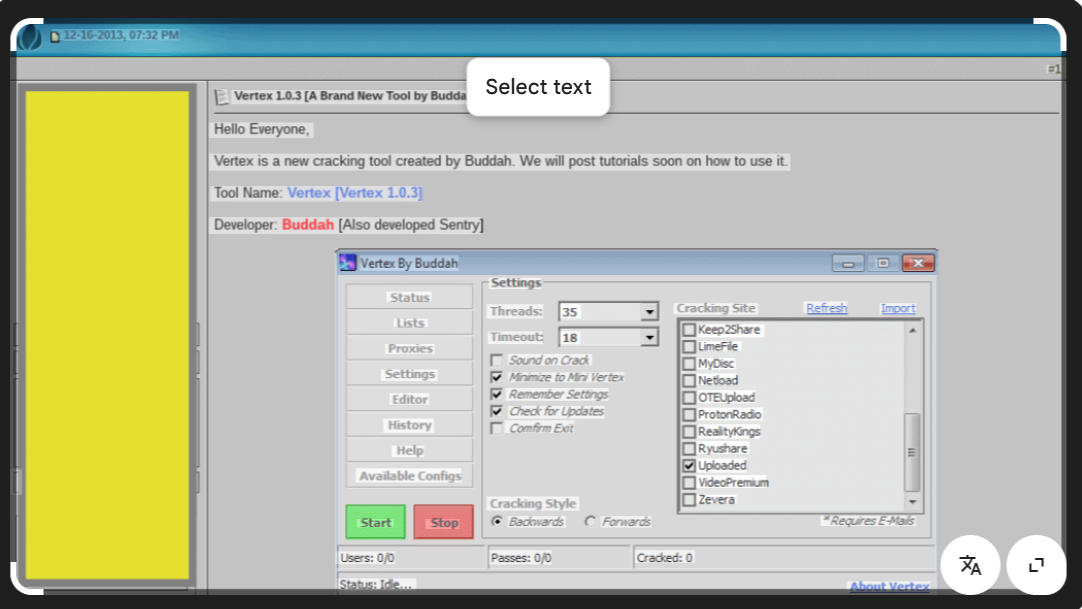
Empower Your Security Arsenal with Cracking Tools Mega Pack 2026 #3
Short Intro: Cracking Tools Mega Pack 2026 #3 serves as an essential toolkit for cybersecurity enthusiasts and professionals aiming to conduct thorough penetration testing and threat simulations. It focuses on providing a one-stop solution for identifying and exploiting system weaknesses to enhance overall digital security. The standout USP lies in its modular design, allowing customization […]
Master Wi-Fi Password Recovery with Tenorshare Wi-Fi Password Key 2026
Short Intro: Empower your cybersecurity efforts. Master Wi-Fi password recovery with Wi-Fi Password Key 2026, a specialized tool for recovering Wi-Fi passwords effortlessly. Whether for personal recovery or professional audits, it provides accurate results without network disruption. Its unique USP is the blend of speed and security, ensuring users regain control over their wireless environments […]