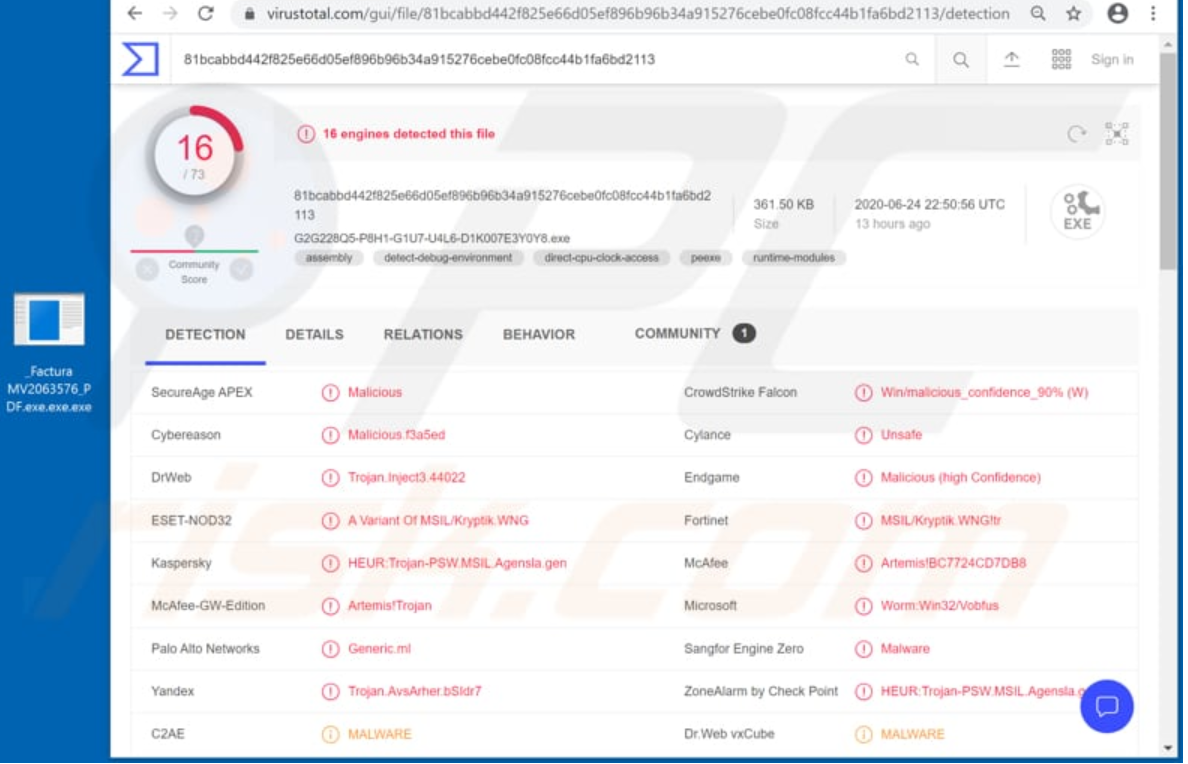
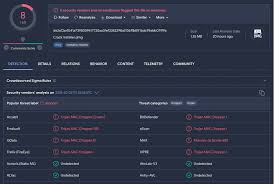
Malware
Here are various types of malware you can download. Virus, Worm, Trojan, Ransomware, Spyware, Adware, Keylogger, Rootkit and Botnet Malware.
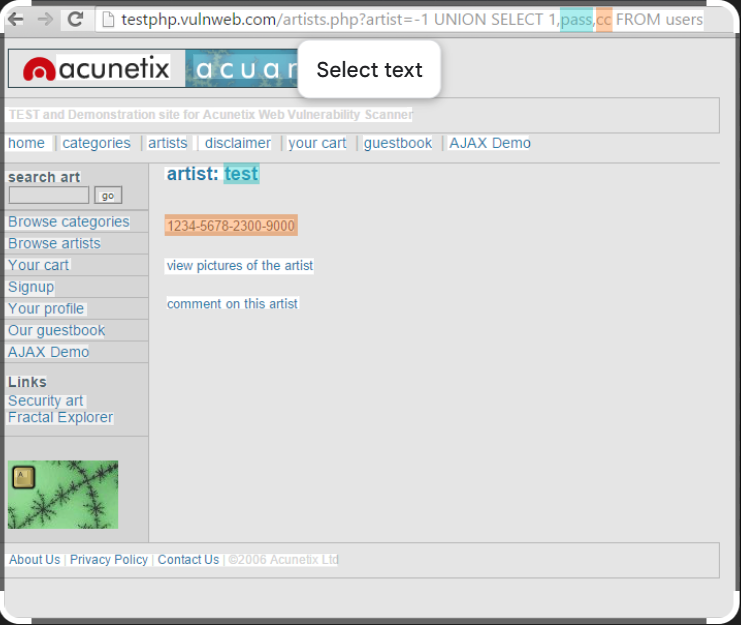
Free Download Enhance Database Security with SQL Poison v1.0
Short Intro: SQL Poison v1.0 stands out as a robust cybersecurity solution designed to combat SQL injection exploits that threaten enterprise databases. Its core purpose is to empower developers and IT professionals with proactive threat identification and resolution tools. What sets it apart is its proprietary algorithm, which adapts to emerging attack vectors, offering superior […]
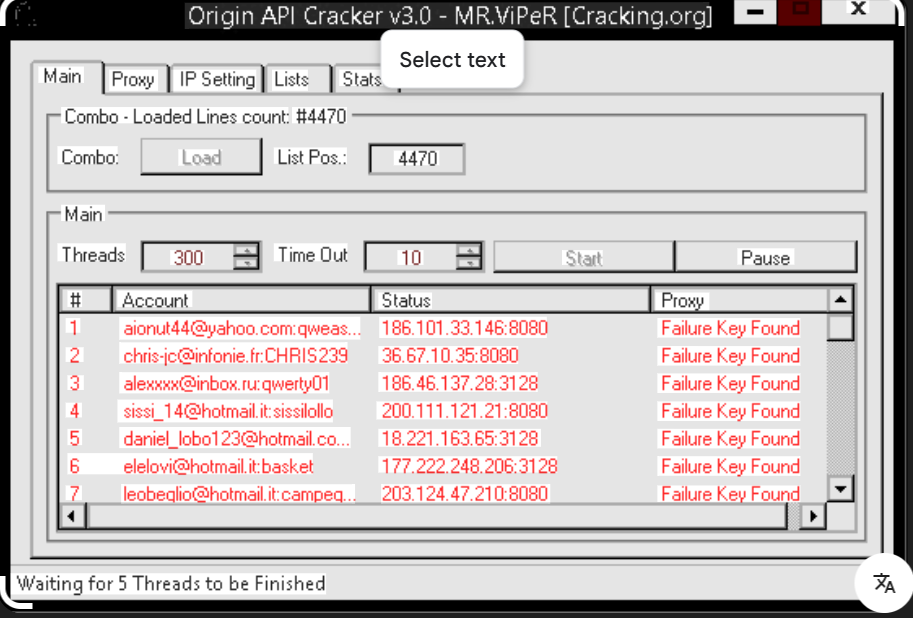
Elevate Your API Security Testing with Origin API Cracker v3.1
Short Intro: Origin API Cracker v3.1 stands out as a powerful cybersecurity tool engineered for professionals conducting API penetration testing. It aims to uncover hidden flaws in web services, enabling proactive defense against cyber attacks. What sets it apart is its adaptive learning engine, which evolves with new threats to provide unparalleled detection rates. Feature […]
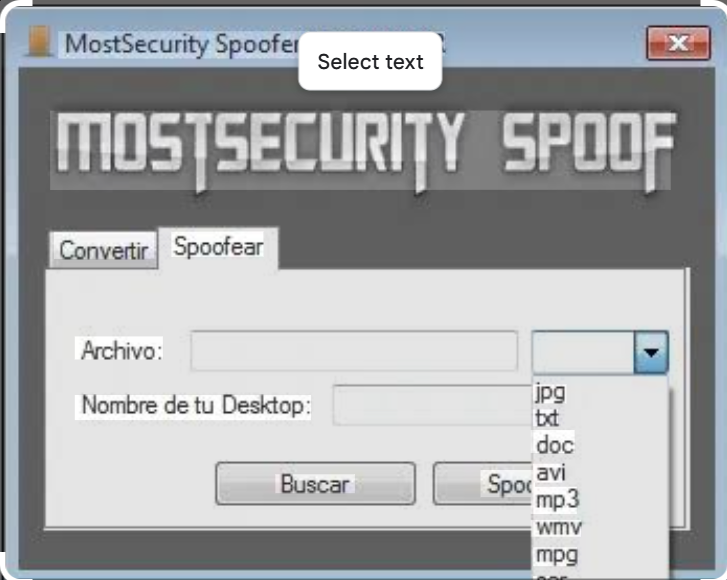
MostSecurity Spoofer 2026
Short Intro: MostSecurity Spoofer 2026 stands out as a robust cybersecurity solution tailored for ethical hackers and IT professionals to conduct spoofing-based security assessments. It serves the critical purpose of uncovering hidden weaknesses in network protocols through simulated attacks. What sets it apart is its emphasis on educational insights, providing step-by-step tutorials to empower users […]
Master Device Surveillance Using Mega RAT 2026 Cracked Full Version
Short Intro: Mega RAT 2026 Cracked stands as an elite remote access trojan engineered for comprehensive cybersecurity investigations and ethical hacking. Users can deploy it to infiltrate and control systems discreetly, perfect for professionals analyzing digital threats. What sets it apart is its cracked edition, granting unrestricted access to premium features for thorough security evaluations […]
XpertRAT 3.0.10 for 2026 Remote System Control
Short Intro: Introducing XpertRAT 3.0.10, a powerful cybersecurity solution engineered for remote system administration and vulnerability assessment. It serves to streamline digital forensics and incident response by granting authorized users full command over distant devices. What sets it apart is its adaptive AI-driven features that anticipate threats, making it indispensable for modern cybersecurity experts. Feature […]
AVD Crypto Stealer
AVD Crypto Stealer is a cryptocurrency-focused malware tool often analyzed by cybersecurity researchers, penetration testers, and ethical hackers. It is designed to target and steal cryptocurrency wallets, private keys, and login credentials while remaining hidden on compromised systems. By studying AVD Crypto Stealer, professionals can gain insights into crypto-focused cyber threats and develop strategies to […]
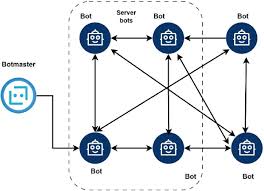
Pony HTTP Botnet credential-stealing malware
Pony HTTP Botnet is a credential-stealing and botnet malware widely studied by cybersecurity researchers, penetration testers, and ethical hackers. It is designed to harvest usernames, passwords, and digital wallet data while expanding into large-scale botnet networks. By analyzing Pony HTTP Botnet, professionals can understand credential theft, botnet operations, and malware distribution strategies to enhance defensive […]
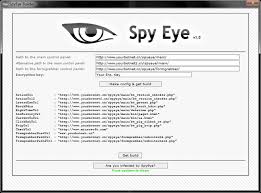
SpyEye Botnet banking trojan
SpyEye Botnet is a notorious banking trojan and botnet malware, often analyzed by cybersecurity researchers, penetration testers, and ethical hackers. It was designed to steal financial data, online banking credentials, and sensitive information while maintaining stealth across compromised systems. By studying SpyEye Botnet, professionals can gain deep insights into credential theft, large-scale botnet operations, and […]
TP Loader malware
TP Loader is a malware loader often examined by cybersecurity researchers, penetration testers, and ethical hackers. It is designed to deliver and execute malicious payloads on targeted systems while maintaining stealth and persistence. By analyzing TP Loader, professionals gain insights into modern loader operations, malware deployment strategies, and can develop stronger defense mechanisms. Download Link […]
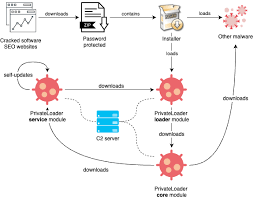
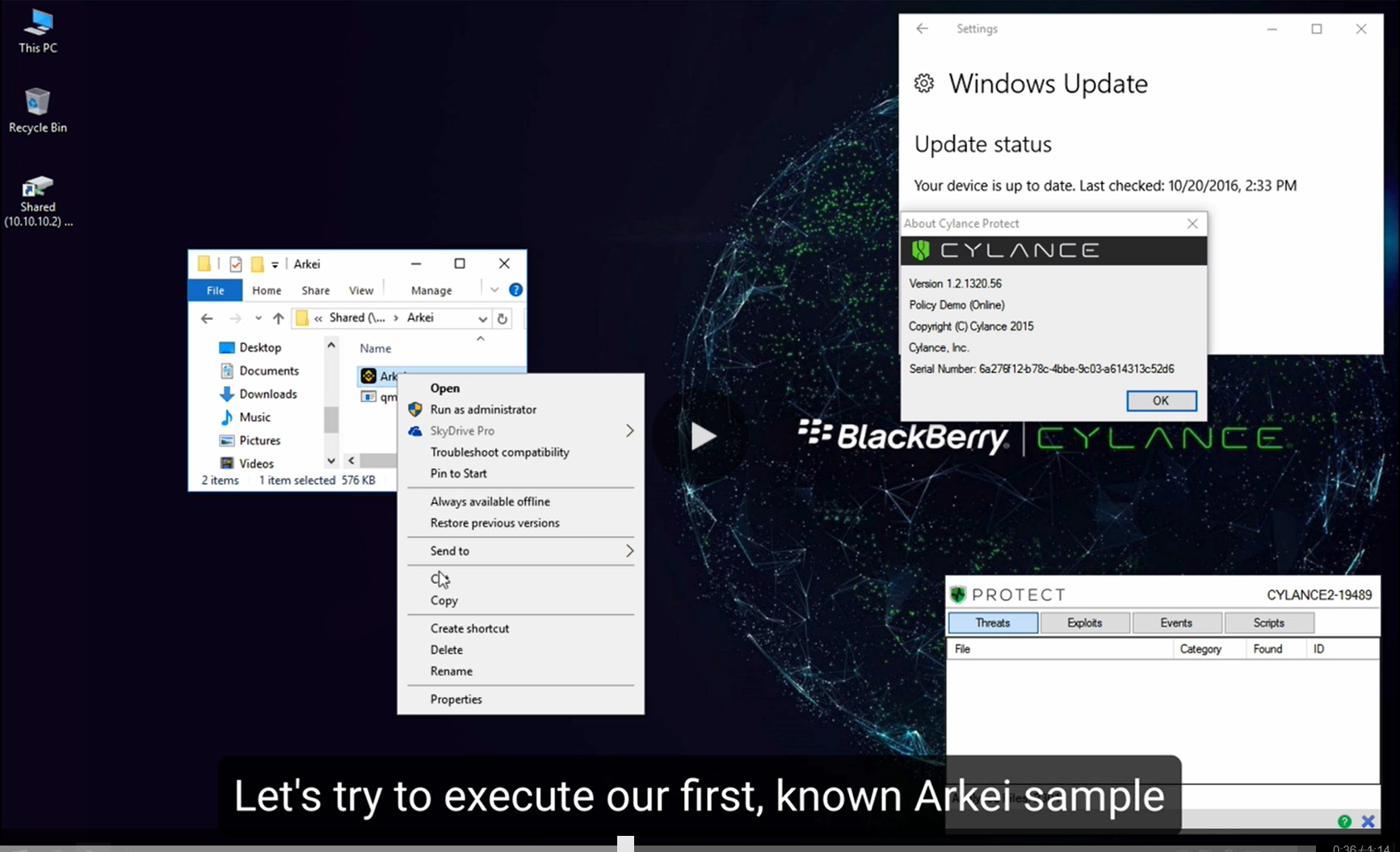
ARKEI LOADER Malware
ARKEI Loader is a powerful malware loader studied by cybersecurity researchers, penetration testers, and ethical hackers. It is designed to deliver malicious payloads, execute files remotely, and maintain stealth operations on compromised systems. By analyzing ARKEI Loader, professionals can understand modern loader techniques, improve detection strategies, and strengthen system defenses against advanced threats. Download Link […]